Hackers and hacking
Hackers can be broadly categorized into several types with unique motives, skills, and methods. Understanding these different types of hackers is essential for individuals and organizations to protect against the various cybersecurity threats they pose. Knowing the workings of different kinds of hackers can enable organizations to anticipate potential cybersecurity threats and create better strategies to secure their systems.
As technology continues to evolve, new types of hackers may emerge. By staying informed about the latest trends and the methods hackers use, individuals and organizations can remain vigilant and implement proactive security measures. It is essential to have conversations about different types of hackers to understand an organization’s threats and foster a security culture in which individuals know the risks and take measures to protect their digital assets.
White hat/ethical hacker
A white hat or ethical hacker is an individual who applies their expertise in computer systems to identify and expose vulnerabilities in information security protocols, with the consent and knowledge of the system owner. Unlike black hat hackers, who engage in malicious activities, white hat hackers typically provide their services as penetration testers, simulating attacks on information systems to help organizations strengthen their security defenses. These professionals use their technical skills to uncover weaknesses in computer networks, software applications, and other digital infrastructures to improve the security of the systems they are testing.
Black hat hacker
A black hat hacker is an individual who exploits vulnerabilities in a computer system for personal gain or malicious intent without the knowledge or consent of the system’s owner. These individuals are involved in criminal activities, such as stealing confidential information, spreading malware, or even blackmailing individuals or organizations for financial gain. Black hat hackers are the driving force behind the widespread proliferation of cybercrime and pose a significant threat to global cybersecurity.
The term black hat was inspired by Western movies, in which the antagonists often wore black hats to symbolize their evil intentions. Black hat hackers use various techniques, including social engineering, phishing, and brute force attacks, to gain unauthorized access to computer systems. They exploit software, hardware, and human behavior weaknesses to bypass security measures and steal sensitive data.
Gray hat hacker
A gray hat hacker is an individual who falls somewhere between a black hat and a white hat hacker. These individuals typically hack into a computer system to identify vulnerabilities, but their intentions may not always be clear. Some gray hat hackers may notify a system owner of their discovered weakness and offer to fix it for a fee. Other gray hat hackers may publish their findings to the internet to showcase their skills or force a vendor to fix a software package. However, it is essential to note that hacking without the permission of the information system owner is illegal and can result in severe consequences. Even gray hat hackers with good intentions may be subject to legal action if they do not have explicit permission to test or assess a system’s security.
Blue hat hacker
A blue hat hacker is an information security professional invited by software or hardware vendors to test their products for vulnerabilities. Blue hat hackers are similar to white hat hackers in that they are committed to improving the security of computer systems and protecting against cyber threats. Their testing involves identifying potential security flaws or bugs that attackers could exploit. By finding these vulnerabilities before the product is released, vendors can address them and improve the security of their products.
Script kiddie
A script kiddie is an individual who uses automated hacking tools and scripts developed by other, more skilled hackers to attack computer systems. These individuals often lack the knowledge and experience to create tools or develop sophisticated attack methods, so they rely on pre-existing scripts and tools to carry out their attacks. This access to tools means that even individuals with minimal technical knowledge can launch attacks on a computer system. Script kiddies are often motivated to cause chaos. However, their lack of knowledge and experience can often result in unintended damage or even compromise their computer systems.
Experienced hackers know how to avoid detection and cover their tracks, making it difficult for law enforcement to apprehend them. On the other hand, script kiddies may be much easier to track down because they lack this skill set. While script kiddies may threaten computer systems, their lack of skill and knowledge limits their ability to carry out sophisticated attacks. However, their impact can still be substantial.
Hacktivist
A hacktivist is an individual who uses their computer security knowledge to promote a political or social agenda by attacking organizations that they believe represent a threat to society. While hacktivists may use similar techniques to black hat hackers, their motivations and goals are different. Hacktivists often launch cyber-attacks against government agencies, corporations, or other organizations that they believe are engaging in unethical or illegal activities. They may deface websites, steal confidential information, or use other cyber vandalism to draw attention to their cause.
Nation-state attacker
A nation-state attacker is an individual or group sponsored by a government to carry out cyber-attacks on other countries, organizations, or individuals. These adversaries are highly skilled and have access to significant resources, including advanced technology and funding. Nation-state activities are best described as cyber warfare, where the attacker is motivated to engage in espionage and sabotage against another country or target. Nation-state actors may seek to compromise military targets, critical infrastructure, political organizations, or private sector/non-profit intellectual property. Their motivations may range from political or economic gain to national security concerns or even acts of terrorism.
Nation-state attackers often use sophisticated and advanced techniques, including zero-day exploits, social engineering, and APTs, to infiltrate their targets’ computer systems. Nation-state attacks pose a significant threat to global cybersecurity and can have far-reaching consequences. Therefore, governments, organizations, and individuals must remain vigilant against these threats and take appropriate measures to protect themselves.
Penetration testing
Penetration testing is an authorized simulation of an information system attack designed to identify vulnerabilities a black hat hacker could exploit. It is an essential component of an information security program and helps organizations find hidden vulnerabilities that cannot be easily detected through automated means.
While many organizations implement vulnerability assessment tools, penetration testing is crucial because it allows information security professionals to systematically break into an information system even when a vulnerability scanner has not found any vulnerabilities. The penetration testing process requires highly skilled and experienced professionals to use their knowledge of information security to assess the security posture of a system.
A penetration testing engagement conducted by a white hat or ethical hacker can include social engineering activities. Those activities may consist of collecting trash from trash cans and dumpsters to look for passwords and intellectual property, pretending to be a helpdesk technician to retrieve user passwords, and launching social engineering attacks such as phishing and spear-phishing. Penetration testing can also include web-based application attacks, vulnerability scanning, port scanning, and more. The penetration testing process is designed to simulate a real-world attack and identify the vulnerabilities that attackers could potentially exploit to gain unauthorized access to a system or sensitive data.
The results of a penetration testing engagement are used to inform information security program stakeholders, including executives, IT professionals, and developers, about the vulnerabilities that have been identified and provide recommendations on how to remediate them. Organizations can improve their overall security posture and reduce the risk of a successful cyber-attack by identifying and addressing vulnerabilities before they can be exploited. Organizations should consider incorporating penetration testing into their overall testing methodology to ensure the security of their systems and data.
Cybercrime
Cybercrime is any criminal activity involving a computer, either as the target or as a tool to carry out the crime. Cybercrime can be committed by individuals and organized criminal gangs, significantly impacting the global economy. The threat of cybercrime is increasing at an alarming rate. According to Cybersecurity Ventures, the cost of cybercrime is expected to reach $8 trillion by 2023 and is projected to grow to $10.5 trillion by 2025. These staggering numbers highlight the urgent need for organizations and individuals to take proactive steps to protect themselves against cyber threats.
One of the most common types of cybercrime is fraud and financial crime. These crimes involve the misrepresentation of facts intending to manipulate another individual or organization into doing or not doing an activity that causes a financial loss. Computer fraud can occur in various ways, including altering, suppressing, destroying, or exfiltrating electronic data. Forms of computer fraud include identity theft, extortion, and bank fraud.
Cyber extortion is another form of cybercrime that occurs when an organization is subjected to repeated attacks by an attacker who demands money to stop the attacks. These crimes can take the form of Denial of Service (DoS) attacks or ransomware attacks, where the attacker blocks access to a system or data until the victim pays a ransom. Cybercrime is a constantly evolving threat, requiring a coordinated and multi-layered approach to combat. Organizations must take measures to protect their systems and data.
Exploits
Exploits are among the primary tools attackers use to gain unauthorized access to an information system. These techniques take advantage of vulnerabilities in an information system by utilizing custom software, operating system commands, and open source tools.
Web applications are particularly vulnerable to exploitation, with numerous well-defined vulnerabilities cataloged by organizations such as the Open Web Application Security Project (OWASP). For many years, OWASP has maintained a top 10 list of the most pervasive and destructive web application vulnerabilities, providing a valuable resource for developers to understand and mitigate these issues in their applications.
Visiting the OWASP website can provide a wealth of information that can be used to enhance the security of your information and application security programs. By understanding common exploits and vulnerabilities, developers and IT professionals can take proactive measures to prevent attacks and protect against unauthorized access to sensitive information.
Note
For more information on OWASP, please refer to https://owasp.org/Top10/.
The OWASP Top 10 vulnerabilities for 2021 are as follows:
- Broken access control: Broken access control is a vulnerability that occurs when an application fails to properly enforce restrictions on what authenticated users are allowed to do. This flaw can allow attackers to access unauthorized functionality and sensitive data, such as other users’ accounts and confidential files, or modify other users’ data and change access rights. Attackers can exploit these weaknesses to access information or actions they are not authorized to have, resulting in severe consequences for the organization or individuals affected. Developers must implement robust access control mechanisms to prevent unauthorized access and ensure the security of sensitive information.
- Cryptographic failures: Cryptographic failures cover various issues related to cryptography. This category includes using weak or outdated encryption algorithms, insecure key management practices, storing sensitive information in plaintext, and improperly implementing SSL/TLS protocols. Cryptographic failures can lead to serious security breaches and compromise sensitive information’s confidentiality, integrity, and availability. To mitigate these risks, developers are advised to follow best practices for cryptography, including using robust encryption algorithms, secure key management, and proper SSL/TLS implementation.
- Injection: Injection flaws refer to vulnerabilities when an interpreter, such as SQL, OS, XXE, or LDAP, receives untrusted data as part of a command or query. Attackers can exploit these weaknesses by sending hostile data that can deceive the interpreter into executing unintended commands or accessing data without proper authorization. To prevent these attacks, developers must use parameterized queries and input validation to ensure that the interpreter processes only trusted data. Other strategies, such as object-relational mapping tools and special character escaping, can also effectively prevent injection vulnerabilities.
- Insecure design: Insecure design covers various issues related to software design. This category includes weak or ineffective access control mechanisms, lack of encryption or hashing, insecure authentication and session management, and poor error handling and logging. Developers must follow secure design principles to prevent issues such as strong access control mechanisms, secure authentication and session management, and proper error handling and logging. Developers should also regularly review their software design to identify and address any potential vulnerabilities.
- Security misconfiguration: Security misconfiguration highlights the importance of having a secure configuration defined and deployed for all system components, including the application, frameworks, application server, web server, database server, and platform. Secure settings should be defined, implemented, and maintained for each component, as default configurations are often insecure. It is essential to establish and maintain secure configurations to minimize the risk of security breaches, protect sensitive information from unauthorized access or data theft, and prevent system compromise.
- Vulnerable and outdated components: The category of vulnerable and outdated components underscores the risk posed by components such as libraries, frameworks, and other software modules that run with the same privileges as the application. If a vulnerable component is exploited, it can enable attackers to facilitate severe data loss or server takeover. Applications and APIs that use components with known vulnerabilities may weaken application defenses and allow various types of attacks with severe consequences. To prevent these vulnerabilities, it is essential to update components to the latest version that has been appropriately tested and reviewed. Developers should also have a process for monitoring and managing component updates and vulnerabilities.
- Identification and authentication failures: Identification and authentication failures are the risks posed by the incorrect implementation of application functions related to authentication and session management. If authentication and session management functions are implemented incorrectly, attackers can exploit vulnerabilities to compromise passwords, keys, or session tokens. This misconfiguration can enable the attacker to assume the identity of other users temporarily or permanently and to access sensitive information or perform unauthorized actions. To prevent these vulnerabilities, developers should follow best practices related to authentication and session management, including using strong and unique passwords, secure session management, and properly handling sensitive data. Implementing multi-factor authentication and using secure communications protocols can also help to prevent authentication and identification failures.
- Software and data integrity failures: Software and data integrity failures can occur due to a lack of proper validation, input sanitization, or other security measures. Software and data integrity failures can result in severe consequences for an application. Such failures may occur due to coding, bugs, or configuration errors, among other factors. It is essential to implement proper input validation and sanitization and ensure that software components are up to date and that the application and data are adequately backed up. Security testing, including fuzz testing and other automated tools, can also help to identify vulnerabilities and prevent software and data integrity failures.
- Security logging and monitoring failures: Security logging and monitoring failures can lead to difficulties in detecting and responding to security incidents and a lack of visibility into system activity. This vulnerability can enable attackers to carry out attacks undetected and remain on a system for extended periods. To prevent these vulnerabilities, developers should ensure that logging and monitoring functionality is implemented correctly and that logs are stored securely and protected from tampering. Organizations should also have processes in place for regularly reviewing and analyzing logs, as well as for responding to incidents and performing forensic analysis when necessary.
- Server-side request forgery: Server-side request forgery vulnerabilities occur when an attacker can send a request to a server or service from within a targeted application, bypassing any security measures. To prevent these vulnerabilities, developers should ensure that input validation is implemented correctly and that requests can only go to trusted external.
Hacker techniques
Hackers are finding new and more creative ways to breach computer systems and networks as technology advances. From exploiting vulnerabilities in software to tricking users into giving away sensitive information, hackers use a wide range of techniques to carry out their attacks. Understanding these techniques and what measures can be taken to prevent them is essential. This section will explore common hacker techniques.
Password cracking
Password cracking is a technique attackers use to gain unauthorized access to a system or application. This technique involves using specialized software to recover passwords transmitted over the network, stored in password databases, or implemented within application software. Attackers often use automated guessing methods, such as dictionary attacks, to crack passwords. Dictionary attacks involve trying common passwords, such as password or 123456, to guess the correct password. Other password-cracking methods include brute-force attacks, where the attacker tries every possible combination of characters until a valid password is found.
It is important to use strong and complex passwords that are difficult to guess to prevent password-cracking attacks. Passwords should be changed regularly and should not be reused across multiple accounts. Additional measures, such as multi-factor authentication and password denylisting, can also help to prevent password cracking attacks.
Let’s now look at some of the password cracking tools that we can use:
- Brutus: http://sectools.org/tool/brutus
- RainbowCrack: http://sectools.org/tool/rainbowcrack
- Wfuzz: http://sectools.org/tool/wfuzz
- Cain and Abel: http://sectools.org/tool/cain
- John the Ripper: http://sectools.org/tool/john
- THC Hydra: http://sectools.org/tool/hydra
- Medusa: http://sectools.org/tool/medusa
- Ophcrack: http://sectools.org/tool/ophcrack
- L0phtCrack: http://sectools.org/tool/l0phtcrack
- Aircrack-NG: https://www.aircrack-ng.org/downloads.html
Vulnerability assessment
Vulnerability assessment scanners are tools that are used to identify potential weaknesses in a network or information system. These scanners use specialized software and databases of known vulnerabilities to scan the network and identify any matches. Once a vulnerability is identified, the tool creates a listing that ties the exposure to a specific IP address, making it easier for administrators to locate and fix the issue.
For administrators, vulnerability assessment scanners can be an essential tool for maintaining the security of their networks and systems. By regularly scanning for vulnerabilities and addressing them promptly, administrators can reduce the risk of successful attacks and protect sensitive data. However, vulnerability assessment scanners can also be used by attackers as a means of identifying potential targets. By scanning a network or system for vulnerabilities, attackers can identify weaknesses that can be exploited to gain unauthorized access or cause damage to the system. By using vulnerability assessment scanners proactively and responsibly, administrators can enhance the security of their networks and systems while minimizing the risk of successful attacks.
Manual vulnerability assessment tests information systems based on a hacker’s knowledge, experience, and intuition to identify potential weaknesses and vulnerabilities that automated scanners may not detect. Unlike automated scanners that use predefined databases of known vulnerabilities, manual testing relies on hackers’ creativity and ingenuity to find vulnerabilities that attackers could exploit. While automated scanners can help identify common vulnerabilities, they may not be able to detect more sophisticated and less well-known vulnerabilities that experienced hackers could exploit.
The following are some of the tools we can use for scanning vulnerability assessment:
- OpenVAS: http://www.openvas.org/
- Burp Suite: https://portswigger.net/burp/freedownload/
- W3af: http://w3af.org/
- NMAP: https://nmap.org/
- Qualys Community Edition: https://www.qualys.com/community-edition/
Keystroke logging
Keystroke logging is a technique attackers use to capture all keystrokes entered on a computer. There are two types of keystroke loggers, namely software-based and hardware-based. Software-based key loggers are installed on a computer through manual and automated mechanisms and can be categorized into hypervisor-based and kernel-based key loggers. The hypervisor-based key logger operates at the hypervisor level of a virtualized infrastructure. It can avoid detection by antivirus tools as it sits below the operating system. On the other hand, the kernel-based key logger operates at the kernel mode of the operating system as a rootkit and can also avoid detection by anti-virus tools as they do not have access to the layer of the operating system.
As the name suggests, hardware-based keyloggers are connected physically to a computer system to capture keystrokes. There are two types of hardware-based key loggers: keyboard hardware and wireless keyboard sniffers. The keyboard hardware-based key logger is connected between a computer and a keyboard. It has internal memory and can intercept keystrokes from the keyboard to the computer. This type of key logger requires physical access to the computer. The wireless keyboard sniffer is a specialized hardware and software device that can intercept keystrokes sent between a wireless keyboard and the computer it is attached to. This type of key logger requires the attacker to be close to the computer being attacked.
Rootkit
A rootkit is a type of malware that a hacker installs to gain control of an operating system. The term root refers to the rootkit giving the attacker root-level access to the system, allowing them to perform various malicious activities. Rootkits are notoriously difficult to detect, as they are designed to operate covertly and remain hidden from the operating system and any security software that may be installed. Rootkits are often used to perform various malicious activities. They achieve this by replacing or modifying critical operating system software, such as device drivers or system libraries, to hide their presence and evade detection. The following figure depicts a computer infected with a rootkit.

Figure 2.1 – Computer infected with a rootkit
There are several types of rootkits, including kernel mode, user mode, and firmware rootkits. Kernel-mode rootkits operate at the lowest level of the operating system, allowing them to intercept system calls and hide their presence from the operating system and any security software. On the other hand, user mode rootkits operate at a higher level of the operating system and are easier to detect but still can hide their presence from many security tools. Finally, firmware rootkits are stored in the firmware of a device, such as a BIOS or a network card, and are particularly difficult to detect and remove.
Spoofing
Hackers use spoofing to deceive users by mimicking another system or person. In a spoofing attack, the hacker may install software or create a system that appears to be a trusted client system to gain unauthorized access to a backend server environment. Alternatively, the hacker may pose as the underlying information system infrastructure to trick unsuspecting users into sharing sensitive information or passwords. The following figure provides an example of a spoofing attack.
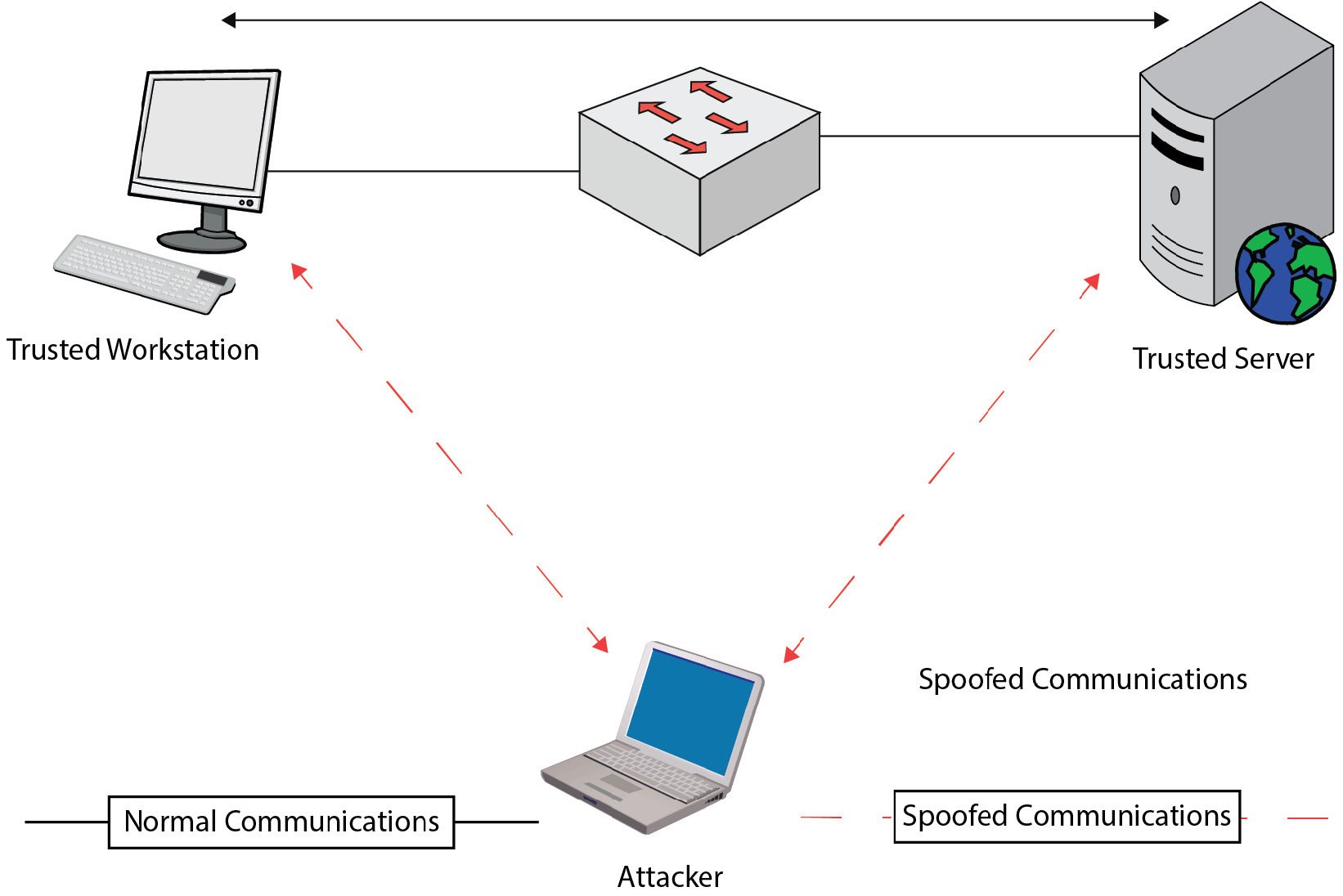
Figure 2.2 – Example spoofing attack
Spoofing attacks can take many forms, including email, IP address, and caller ID. In email spoofing, the attacker forges the From address in an email to make it appear as if it came from a trusted source. In IP address spoofing, the attacker changes the source IP address in an IP packet to make it appear as if it originated from a trusted source. In caller ID spoofing, the attacker manipulates the phone number displayed on the recipient’s caller ID to make it appear that the call is from a trusted source. Spoofing attacks can harvest sensitive company information.
Social engineering
Social engineering is a hacking technique that doesn’t rely on technical tools but manipulates human psychology to gain unauthorized access to sensitive information or systems. It involves deception and persuasion, exploiting an individual’s natural inclination to trust others. Social engineering attackers can use a variety of tactics, such as phishing scams, pretexting, baiting, and water-holing, to gather sensitive information. The following depicts the social engineering life cycle.

Figure 2.3 – The social engineering life cycle
Pretexting
Pretexting is a social engineering attack where the attacker creates a false scenario or pretext to trick the victim into divulging sensitive information. The attacker will typically establish a position of authority, trust, or familiarity to make the victim feel more comfortable and willing to share information. This scenario can include posing as a victim’s company or organization member, a trusted vendor or partner, or even a friend or family member.
One common example of pretexting involves an attacker posing as a victim’s IT department member. The attacker may contact the victim via email, phone, or in person, claiming there is a problem with the victim’s account or computer system. They may then request that the victim provide their username and password to resolve the issue. The victim, thinking they are helping resolve a legitimate problem, may willingly give this information.
However, the attacker has no legitimate reason to request this information and is using it to gain unauthorized access to the victim’s account or system. With this information, the attacker can move further into the organization’s information system and potentially cause damage or steal sensitive information.
Pretexting attacks can be challenging to detect, as the attacker may use sophisticated techniques to create a convincing pretext and establish trust with the victim. It’s essential for individuals and organizations to be aware of these types of attacks and to establish protocols for verifying requests for sensitive information. This verification can include verifying the requester’s identity, checking with a supervisor or IT department, or requiring additional authentication before providing sensitive information.
Phishing
Phishing is a social engineering attack that uses deception and technology to trick users into providing sensitive information such as login credentials, credit card numbers, and personal data. Unlike pretexting, which targets individuals one at a time, phishing campaigns can target millions of users simultaneously, making it a highly effective tactic for hackers.
In a phishing attack, the attacker typically sends an email that appears to be from a trusted source, such as a bank, an online retailer, or a social media site. The email will usually contain a message that creates a sense of urgency or alarm, such as a warning that the user’s account has been compromised or a request to update their account information.
The email may also contain a link or attachment the user is directed to click on. In the case of the link, it will take the user to a fake website. The website looks like a legitimate website but is controlled by the attacker. The phony website will typically prompt the user to enter their login credentials or other sensitive information, which the attacker then captures. In some cases, the phishing email may also contain a malicious attachment that, when opened, installs malware on the user’s computer or device.
Phishing attacks can be challenging to detect, as emails and fake websites can be designed to look very convincing. It’s important for individuals and organizations to be aware of the signs of a phishing attack, such as suspicious email addresses or URLs, and to verify the legitimacy of any requests for sensitive information before responding. Here is an example of a phishing campaign. Notice that the email appears to come from Netflix and generically addresses the user. The link would take the user to the attacker’s website if clicked. The following figure is taken from an actual phishing message.
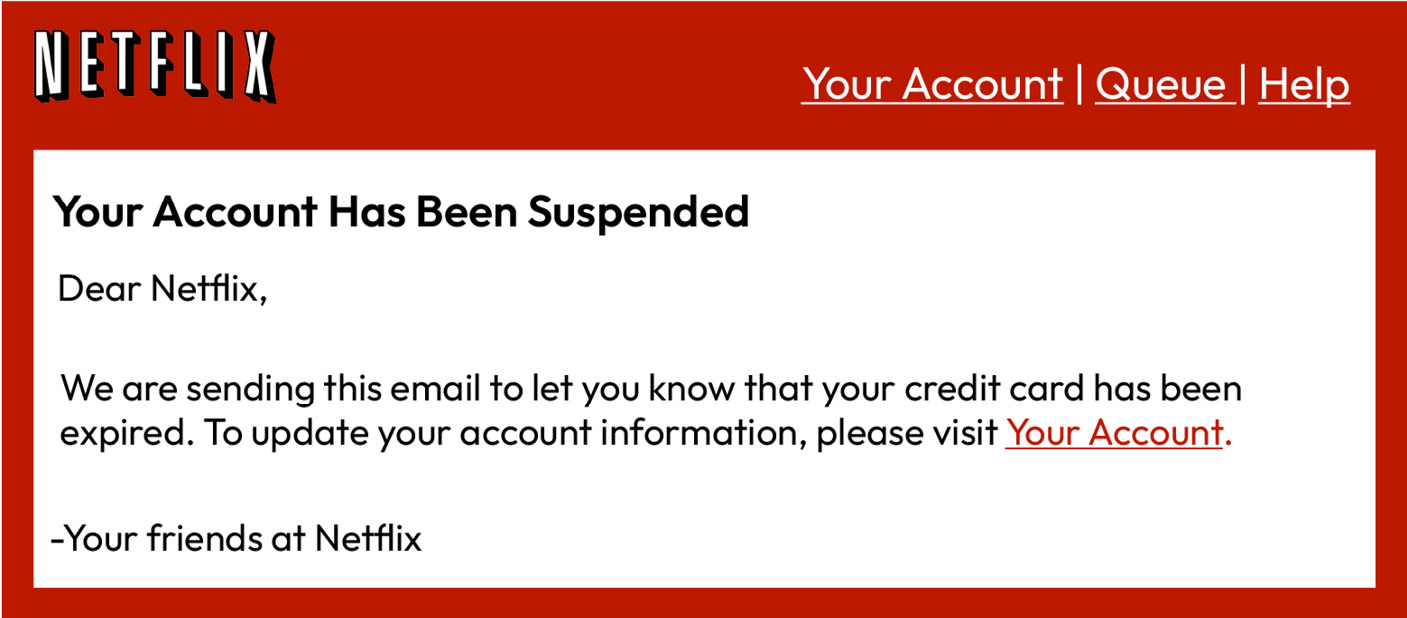
Figure 2.4 – Phishing message example
Spear phishing
Spear phishing is a highly targeted phishing attack focusing on specific individuals or groups rather than sending out mass emails like traditional phishing campaigns. In spear phishing attacks, the attacker performs extensive reconnaissance on the victim to gather personal details to make their attack more convincing.
Unlike phishing campaigns, which typically use generic messages sent out to many potential victims, spear phishing emails are highly customized to the individual victim. The attacker will use their gathered personal details to create a message tailored to the victim’s interests, job position, or personal relationships.
For example, an attacker might send a spear phishing email to an employee at a company, posing as a senior executive and requesting sensitive financial information. The email might include details about a recent company project or event that the attacker has gleaned from the victim’s social media profile or public information online, making the email appear more legitimate.
Spear phishing attacks can be highly effective, as the customized nature of the attack makes it more difficult for victims to identify it as fraudulent. The attacker’s attention to detail and personalization can create a sense of trust between the victim and the attacker, making it more likely that the victim will provide the requested information.
Awareness training to combat phishing
Phishing attacks continue to be a significant threat to organizations of all sizes, and it’s essential to have effective countermeasures in place to combat them. The most effective countermeasure is to raise awareness among your user population about phishing and spear phishing threats.
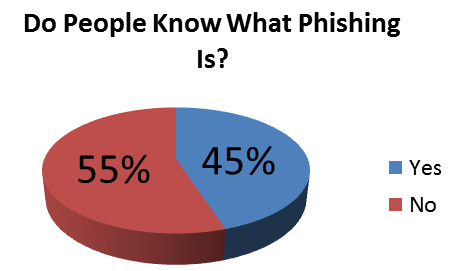
Figure 2.5 – Do your users understand phishing?
As an information security professional, it’s easy to become complacent and assume everyone is already aware of phishing. However, it’s important to remember that other parts of the organization have their specialized work and may not be as familiar with the risks. It’s crucial to communicate the importance of phishing awareness to all organization members, including those in HR, finance, manufacturing, and other departments.
There are several methods for conducting training and raising awareness about phishing threats. One practical approach is to include specific phishing training in your yearly information security training. If you don’t currently conduct annual training, it’s important to start doing so. Another approach is to develop a cycle for communicating with your entire user base via targeted communications such as emails and internal social media. You can create a plan where several communications are used to deliver targeted phishing awareness training.
Conducting phishing exercises is also an effective way to test your user base’s awareness of phishing. You can utilize automated tools to test your user base for their awareness of phishing threats. These tools should allow you to import your user population from your user directory rather than manually inputting them into the tool. You should also be able to build multiple campaigns to target different user groups simultaneously. Additionally, the tool should allow you to track exploited users as part of the training so they can be scheduled for additional training. It’s important to note that users should not be treated negatively if they are determined to need additional training. The process should be positive, and users should feel they are learning a new skill rather than being reprimanded. By implementing these training and awareness strategies, you can help to protect your organization from the devastating consequences of phishing attacks.
Water-holing
Water-holing exploits vulnerabilities in trusted websites frequently used by a particular user or group within an organization. To execute a water-holing attack, the attacker first conducts reconnaissance to identify websites the target users regularly visit. The attacker then attempts to compromise the trusted website, potentially by exploiting vulnerabilities in the website’s code or by compromising a third-party service that the website relies on. Once the website has been compromised, it can be used as a platform to install malware on unsuspecting users’ machines.
The attacker may wait for the users to visit the compromised website, or they may use a spear phishing email to lure the users to the site. The spear phishing email could be designed to appear as if it comes from a trusted source or contain a link to a fake login page that looks like the real thing. Water-holing attacks can be particularly effective because they exploit users’ trust in familiar websites. They can also be difficult to detect because the attack comes from a trusted website rather than a suspicious or unknown source.
Baiting
Baiting uses physical media, such as DVDs or USB drives, to entice users into inserting the drives into their computers. The bait may be disguised as a free software or music download, a coupon or discount offer, or other enticing content. Many users insert removable media into their computers without properly verifying its source or content. The best defense against baiting attacks is to train users about the risks and how to avoid them. Training would include ensuring that users understand the importance of not inserting removable media into their computers unless it comes from a trusted source, such as their employer or a reputable vendor.

























































