Handling the device during seizure is one of the important steps while performing forensic analysis. The evidence is usually transported using anti-static bags, which are designed to protect electronic components against damage produced by static electricity. As soon as the device is seized, care should be taken to make sure that our actions don't result in any data modification on the device. At the same time, any opportunity that can aid the investigation should also not be missed. The following are some of the points that need to be considered while handling an Android device during this phase:
- With increasing user awareness of security and privacy, most devices now have screen lock enabled. During the time of seizure, if there is a chance (for instance, the phone is recovered unlocked), disable the passcode. Some of the devices don't ask the user to reenter the passcode while disabling the lock screen option.
- If the device is unlocked, try to change the settings of the device to allow greater access to the device. The following are some of the settings that can be considered to achieve this:
- Enable USB debugging: Enabling this option gives greater access to the device through the Android Debug Bridge (ADB) connection. We are going to cover the ADB in detail in Chapter 2, Setting Up the Android Forensic Environment. This will greatly aid the forensic investigator during the data extraction process. In Android devices, this option is usually found under Settings | Developer options, as shown in the following screenshot. On newer Android versions starting from 4.2, developer options are hidden by default. To enable them, navigate to Settings | About Phone (or Settings | System | About Phone on Android 8.0 or higher)and tap on the Build number seven times.
- Enable the Stay Awake setting: Enabling this option and charging the device will make the device stay awake; in other words, it doesn't get locked. In Android devices, this option is usually found under Settings | Developer options, as shown in the following screenshot:
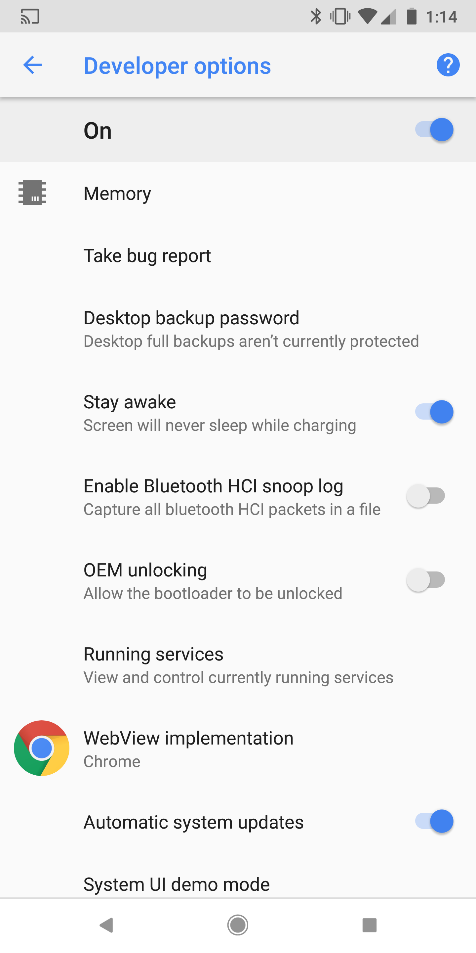
-
- Increase screen timeout: This is the time for which the device will be active once it is unlocked. Depending on the device model, this time can be set up to 30 minutes. In most devices, it can be accessed under Settings | Display | Screen Timeout.
Please note that the location to access these items changes across different versions and models of Android phones and may not be available in all versions.
In mobile forensics, it is of crucial importance to protect the seized device so that our interaction with the evidence (or, for that matter, an attacker's attempt to remotely interact with the device) doesn't change the evidence. In computer forensics, we have software and hardware write blockers that can perform this function. But in mobile forensics, since we need to interact with the device to pull the data, these write blockers are not of any use. Another important aspect is that we also need to prevent the device from interacting with a wireless radio network. As mentioned earlier, there is a high probability that an attacker can issue remote wipe commands to delete all of the data including emails, applications, photos, contacts, and other files on the device.
The Android Device Manager and several other third party apps allow the phone to be remotely wiped or locked. This can be done by signing into the Google account that is configured on the mobile. Using this software, an attacker can also locate the device that could pose a security risk. For all of these reasons, isolating the device from all communication sources is very important.
Have you thought about remote wipe options without using the internet? Mobile Device Management (MDM) software, commonly used by companies to manage corporate devices, can provide remote wipe features just by sending an SMS. Isolating the device from all communication options is crucial.
To isolate the device from a network, we can put the device in Airplane mode if we have access to the device. Airplane mode disables a device's wireless transmission functions such as cellular radio, Wi-Fi, and Bluetooth. However, as Wi-Fi is now available in airplanes, some devices now allow Wi-Fi access in Airplane mode. The following screenshot shows the quick settings available by dragging down the top menu bar from the lock screen:
Note that these toggles are customizable and may not be available on every device; some devices may also require the device to be unlocked to make these changes.
An alternate solution would be to use a Faraday bag or RF isolation box, as both effectively block signals to and from the mobile phone. One concern with these isolation methods is that, once they're employed, it is difficult to work with the phone because you cannot see through it to use the touchscreen or keypad. For this reason, Faraday tents and rooms exist, as shown in the following screenshot:
Even after taking all of these precautions, certain automatic functions such as alarms can still trigger. If such a situation is encountered, it must be properly documented.
 Germany
Germany
 Slovakia
Slovakia
 Canada
Canada
 Brazil
Brazil
 Singapore
Singapore
 Hungary
Hungary
 Philippines
Philippines
 Mexico
Mexico
 Thailand
Thailand
 Ukraine
Ukraine
 Luxembourg
Luxembourg
 Estonia
Estonia
 Lithuania
Lithuania
 Norway
Norway
 Chile
Chile
 United States
United States
 Great Britain
Great Britain
 India
India
 Spain
Spain
 South Korea
South Korea
 Ecuador
Ecuador
 Colombia
Colombia
 Taiwan
Taiwan
 Switzerland
Switzerland
 Indonesia
Indonesia
 Cyprus
Cyprus
 Denmark
Denmark
 Finland
Finland
 Poland
Poland
 Malta
Malta
 Czechia
Czechia
 New Zealand
New Zealand
 Austria
Austria
 Turkey
Turkey
 France
France
 Sweden
Sweden
 Italy
Italy
 Egypt
Egypt
 Belgium
Belgium
 Portugal
Portugal
 Slovenia
Slovenia
 Ireland
Ireland
 Romania
Romania
 Greece
Greece
 Argentina
Argentina
 Malaysia
Malaysia
 South Africa
South Africa
 Netherlands
Netherlands
 Bulgaria
Bulgaria
 Latvia
Latvia
 Australia
Australia
 Japan
Japan
 Russia
Russia


















