Recognizing breaches
If you follow the news, you are probably aware that there is no shortage of breaches nowadays. They are happening so frequently that it is not uncommon for several breaches to occur weekly or even daily. What is even scarier is that these are just the ones that we hear about. To give you an idea of how serious the issue has become, the following list has some of the more notable breaches that are documented on Wikipedia’s List of data breaches page. There are many sources on the internet identifying top breaches, but Wikipedia has the most comprehensive information we have found with references to each of the listings:
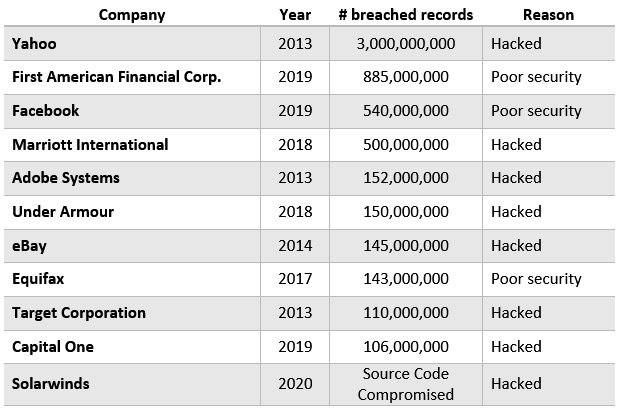
Figure 1.8 – Wikipedia list of data breaches
You can find the source of the preceding screenshot at https://en.wikipedia.org/wiki/List_of_data_breaches and a list of security incidents here: https://en.wikipedia.org/wiki/List_of_security_hacking_incidents.
As you review the breaches and understand how they occurred, you will see a common trend where, for the most part, the breach occurred from hacking or poor security practices. You might also notice that other common methods of breaches include lost or stolen equipment. These statistics are alarming, and they indicate how critical it is to secure and harden our systems as best as possible.
It is also important to point out that the tactics of some malicious actors are not to breach records but to hold a company at ransom for a large payout. One of the more notable ransomware attacks recently was against Colonial Pipeline, which is one of the largest fuel pipelines in the US. This ransomware was so impactful that it forced the company to shut down its fuel distribution operations, causing gas shortages for consumers throughout the east coast. Another attack becoming more common is that of the supply chain, where hackers look to compromise a vendor that can then in turn compromise all its downstream customers. One of the most infamous such attacks was the SolarWinds cyberattack, where hackers implanted malicious code into their software, which was received by thousands of customers. Once installed, hackers were provided the ability to infiltrate customers’ networks.
To give you an idea of the importance of securing and hardening your environment, the International Business Machines Corporation (IBM) data breach report of 2021 provides some data points that are not to be taken lightly. In 2021, the average cost of a data breach was $4.24 million, which is the highest average cost since the report began. The most common initial attack vector was compromised credentials. In addition, the report shows that the average cost of a user record from a data breach is $161 per record. A quick calculation of this multiplied by 100,000 customers calculates a potential loss estimated at $16.1 million. When you look at the number of breached records shown in Figure 1.8, you will understand how this could be extremely damaging to a business’s value and reputation.
You can download and view more details on the IBM Cost of a Data Breach Report here: https://www.ibm.com/security/data-breach.
Tip
An interesting site for reference is Have I Been Pwned. This site will show you whether any of your accounts that use your email address have ever been breached and, if so, where the breach was: https://haveibeenpwned.com/. You can also sign up for notifications for any breaches using your email address or submit a specific domain to be notified on.
There are many sources available where you can view security news and follow the latest trends and best practices. Here are some recommended resources to help keep you up to date with the latest happenings in the security world today:
- DarkReading: https://www.darkreading.com/
- Cyware: https://cyware.com/cyber-security-news-articles (recommended phone app)
- Cybersecurity Insiders: https://www.cybersecurity-insiders.com/
- CSO: https://www.csoonline.com/
- Krebs on Security: https://krebsonsecurity.com/
- The Hacker News: https://thehackernews.com/
- Darknet Diaries podcast: https://darknetdiaries.com/
- Risky Business podcast: https://risky.biz/
Next, we will discuss the security challenges we face in today’s world and within the enterprise.

























































