Routing
The point-to-point type of networks are great if you want to connect two networks together over a static, encrypted tunnel. If you only have a small number of endpoints (fewer than four), then routing is far easier than using a client/server setup as described in Chapter 2, Client-server IP-only Networks.
Getting ready
For this recipe, we will use the following network layout:
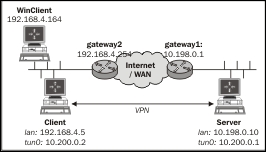
Install OpenVPN 2.3.9 or higher on two computers. Make sure the computers are connected over a network. For this recipe, the server computer was running CentOS 6 Linux and OpenVPN 2.3.9 and the client was running Windows 7 64 bit and OpenVPN 2.3.10. We'll use the secret.key file from the OpenVPN secret keys recipe here.
How to do it...
- First, establish the connection, but also make sure OpenVPN has daemonized itself:
[root@server]# openvpn \ --ifconfig 10.200.0.1 10.200.0.2 \ --dev tun --secret secret.key \ --daemon --log /tmp/openvpnserver.log
- Then, launch the client-side OpenVPN process:
[client]$ openvpn \ --ifconfig 10.200.0.2 10.200.0.1 \ --dev tun --secret secret.key \ --remote openvpnserver \ --daemon --log /tmp/openvpnclient.log
- The connection is established:
[server]$ tail -1 /tmp/openvpnserver.log Initialization Sequence Completed
Now we add routing:
- On the server side, we add a static route:
[root@server]# route add -net 192.168.4.0/24 gw 10.200.0.2 - On the client side, we need to do two things:
Make sure that you have the IP traffic forwarding enabled. On Linux, this can be achieved using the following:
[root@client]# sysctl -w net.ipv4.ip_forward=1Note
Note that this setting does not survive a reboot of the system.
On the Windows client on the client-side LAN, make sure there is a route back to the OpenVPN server:
C:> route add 10.200.0.0 mask 255.255.255.0 192.168.4.5Note
Here,
192.168.4.5is the LAN IP address of the OpenVPN client. - From the server, we can now ping machines on the client LAN. First, ping the LAN IP of the OpenVPN client:
[root@server]# ping -c 2 192.168.4.5 PING 192.168.4.5 (192.168.4.5) 56(84) bytes of data. 64 bytes from 192.168.4.5: icmp_seq=0 ttl=64 time=31.7 ms 64 bytes from 192.168.4.5: icmp_seq=1 ttl=64 time=31.3 ms --- 192.168.4.5 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1000ms rtt min/avg/max/mdev = 31.359/31.537/31.716/0.251 ms, pipe 2
- Then, ping the LAN IP of a machine on the OpenVPN client LAN:
[root@server]# ping -c 2 192.168.4.164 [server]$ ping -c 2 192.168.4.164 PING 192.168.4.164 (192.168.4.164) 56(84) bytes of data. 64 bytes from 192.168.4.164: icmp_seq=0 ttl=63 time=31.9 ms 64 bytes from 192.168.4.164: icmp_seq=1 ttl=63 time=31.4 ms --- 192.168.4.164 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1001ms rtt min/avg/max/mdev = 31.486/31.737/31.989/0.308 ms, pipe 2
How it works...
In our network setup, the LAN we want to reach is behind the OpenVPN client, so we have to add a route to the server:
[server]$ route add -net 192.168.4.0/24 gw 10.200.0.2
On the client side, we need to do two things:
- Make sure that the routing is enabled. If you want routing to remain enabled after a reboot, edit the
/etc/sysctl.cnffile:net.ipv4.ip_forward = 1
- We also need to make sure that there is a route back to the OpenVPN server on the client LAN. This can be done by adding a route to the LAN gateway or by adding a static route to each of the machines on the client LAN. In this recipe, we added a route to a Windows client that is in the same LAN as the OpenVPN client:
C:> route add 10.200.0.0 mask 255.255.255.0 192.168.4.5
Here, 192.168.4.5 is the LAN IP address of the OpenVPN client.
There's more...
Let's discuss a bit about routing issues and how to automate the setup.
Routing issues
On the OpenVPN users mailing list, a large number of the problems that are reported have something to do with routing issues. Most of them have little to do with OpenVPN itself, but more with understanding the routing and the flow of packets over the network. Chapter 7, Troubleshooting OpenVPN - Routing, provides some recipes to diagnose and fix the most common routing problems.
Automating the setup
It is also possible to add the appropriate routes when the tunnel first comes up. This can be done using the --route statement:
[server]$ openvpn \ --ifconfig 10.200.0.1 10.200.0.2 \ --dev tun --secret secret.key \ --daemon --log /var/log/openvpnserver-1.5.log \ --route 192.168.4.0 255.255.255.0
Note that on the client LAN, the route back to the server still has to be set manually.
See also
- The Three-way routing recipe, later on in this chapter, where a more complicated setup using three remote sites is explained
- Chapter 7, Troubleshooting OpenVPN - Routing


























































