The significance of digital identities in the modern IT landscape
In today’s digital age, digital identities are essential for accessing IT-related services. An identity strategy goes beyond just provisioning and adding or removing access but determines how an organization manages accounts, standards for validation, and what a user or service can access.
Reporting on activities that affect identity life cycles is also an essential component of an identity strategy. A well-formed identity infrastructure is based on guidelines, principles, and architectural designs that provide organizations with interoperability and flexibility to adapt to ever-changing business goals and challenges.
An effective identity infrastructure should be based on integration and manageability standards while being user-friendly and secure. In order to simplify the end user experience, the infrastructure should provide easy-to-use and intuitive methods for managing and accessing digital identities. With a well-designed and implemented identity infrastructure, organizations can reduce the risk of unauthorized access to their IT resources and improve their overall security posture. Additionally, a standardized identity infrastructure can facilitate collaboration between organizations and make it easier for users to access resources across multiple organizations.
Also, with the growing trend of organizations seeking to invest in cloud services to achieve modernization, cost control, and new capabilities, IAM capabilities have become the central pillar for cloud-based scenarios. Azure AD has become a comprehensive solution that addresses these requirements for both on-premises and cloud applications. The following section provides insights into common scenarios and demonstrates how Azure AD can help with planning and preparing organizations to use cloud services effectively.
Modernizing your IAM with Microsoft Azure AD
Microsoft’s Azure AD is a cloud-based IAM service designed to help organizations manage access to resources across different cloud environments. With Azure AD, organizations can control access to cloud applications, both Microsoft and non-Microsoft, through a single identity management solution. This enables employees to access the tools and information they need from any device, anywhere in the world, with increased security and efficiency.
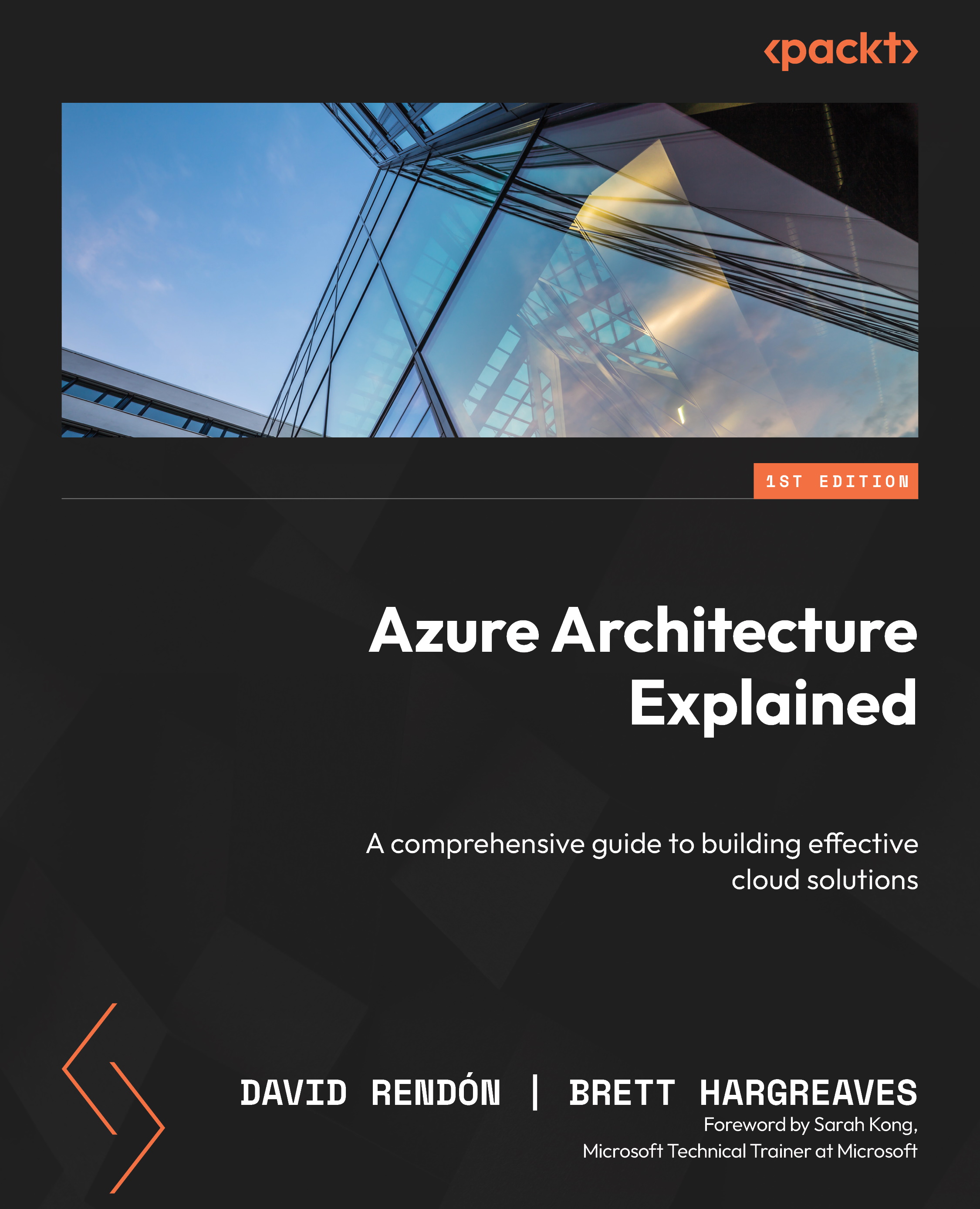
The following figure highlights the structure of Azure AD.
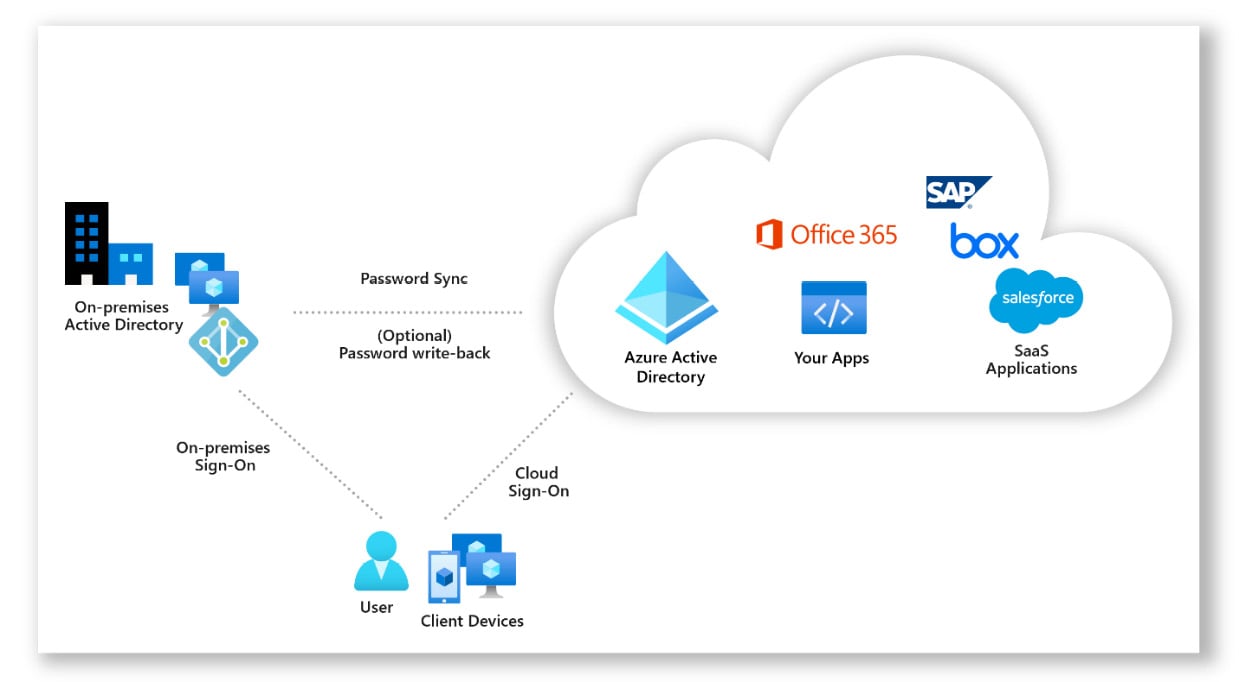
Figure 1.1 – Azure AD
Azure AD provides several benefits for organizations looking to modernize their IT infrastructure. It offers seamless integration with other Azure services and enables IT administrators to manage user identities and security policies and access resources from a central location. Additionally, it provides MFA and Conditional Access policies to help protect against identity-based attacks.
Organizations can also use Azure AD to manage access to third-party applications, including Software as a Service (SaaS) applications, such as Salesforce, Box, and Dropbox, providing a consistent and secure user experience across different cloud environments.
However, IAM tasks can significantly burden IT departments, taking up valuable time that could be spent on higher-value work. A crucial piece of an IAM solution is its life cycle management capabilities.
Life cycle management
Provisioning new users can be tedious, requiring administration and configuration across multiple systems. Users may have difficulty obtaining the necessary access to perform their jobs, causing delays and inefficiencies.
For example, the IT team of SpringToys, an online retail organization, may have to access and configure multiple identity utilities and repositories to onboard a new user for online services, making the process even more complicated. With an ad hoc manual method, achieving stringent levels of control and compliance with necessary regulatory standards can be challenging. Each time an employee needs to access an IT service, IT staff must manually handle the request and perform administrative tasks to enable access, creating inefficiencies and delays that impact productivity. By implementing a robust IAM solution, organizations can reduce the burden on IT staff, streamline IAM processes, and improve security and compliance posture.
Effective management of the identity life cycle can bring numerous benefits to organizations, including reducing the time and cost of integrating new users and improving security by controlling access to resources centrally.
By maximizing the investments in existing on-premises identities, organizations can extend them to the cloud, reducing the time for new users to access corporate resources and streamlining the provisioning process. Consistent application of security policies enhances the security posture and reduces exposure to outdated credentials. It also minimizes business interruptions and reduces the time and cost required to enable applications to be accessible from the internet.
Additionally, the increased capacity of IT to develop core application features and the ability to delegate specific administration tasks can lead to increased flexibility and auditing capabilities, enhancing the overall efficiency and effectiveness of IAM solutions.
Leveraging the Microsoft Cloud Adoption Framework
If your organization is on its journey of adopting Azure IAM, consider leveraging the Microsoft Cloud Adoption Framework (CAF) for Azure (https://bit.ly/azurecaf), a guide that helps organizations create and implement strategies for cloud adoption in their business.
It provides a set of best practices, guidance, and tools for different stages of cloud adoption, from initial planning to implementation and optimization. The framework is designed to help organizations develop a comprehensive cloud adoption plan, create a governance structure, and identify the right tools and services for their specific business needs.
The CAF comprises multiple stages: strategy, plan, ready, migrate, innovate, secure, manage, and govern. Each stage includes a set of recommended practices, tools, and templates that help organizations to assess their readiness, build a cloud adoption plan, migrate applications and data to the cloud, and optimize cloud resources.
The following figure highlights the CAF stages:
Figure 1.2 – Microsoft CAF for Azure
The framework is flexible and can be customized to fit an organization’s specific needs. It is designed to work with different cloud services and technologies, including Microsoft Azure, Amazon Web Services (AWS), and Google Cloud.
Also, the CAF includes a specific IAM design area that focuses on providing guidance and best practices for designing secure and scalable IAM solutions in the Azure cloud platform. This includes managing identities, implementing authentication and authorization mechanisms, and establishing proper governance and compliance policies. By following the Azure IAM design principles, organizations can ensure their cloud environments are secure and compliant and effectively manage access to their cloud resources.
Utilize this framework to expedite your cloud adoption process. The accompanying resources can assist you in every stage of adoption. These resources, including tools, templates, and assessments, can be applied across multiple phases: https://bit.ly/azure-caf-tools.
Azure AD terminology, explained
Azure AD is a system used to manage access to Microsoft cloud services. It involves several terms that are important to understand. Identity is something that can be authenticated, such as a user with a username and password or an application with a secret key or certificate. An account is an identity that has data associated with it.
Azure AD supports two distinct types of security principals: user principals, which represent user accounts, and service principals, which represent applications and services. A user principal encompasses a username and password, while a service principal (also referred to as an application object/registration) can possess a secret, key, or certificate.
An Azure AD account is an identity created through Azure AD or another Microsoft cloud service, such as Microsoft 365. The account administrator manages billing and all subscriptions, while the service administrator manages all Azure resources.
The owner role helps manage Azure resources and is built on a newer authorization system, called Azure role-based access control (RBAC). The Azure AD Global Administrator is automatically assigned to the person who created the Azure AD tenant and can assign administrator roles to users.
An Azure tenant is a trusted instance of Azure AD created when an organization signs up for a Microsoft cloud service subscription. A custom domain name can be added to Azure AD to make usernames more familiar to users.
When an Azure AD tenant is created, it comes with a default *.on.microsoft.com domain. A custom domain name such as springtoys.com can be added to the Azure AD tenant to make usernames more familiar to the users.
For example, imagine SpringToys wanting to use Microsoft Azure to store and manage its data. They would need to create an Azure subscription, which would automatically generate an Azure AD directory for them. They would then create Azure AD accounts for each employee who needs access to the company’s data stored in Azure.
Each employee’s Azure AD account would be associated with their Microsoft 365 account, which they use to log in to their work computer and access company resources. The company could also add a custom domain name to Azure AD so that employees can use email addresses with their company’s domain name to log in to their Azure AD account, such as [email protected]. The company would also need to assign roles to each employee’s Azure AD account, such as the owner role or service administrator role, to manage access to Azure resources. In broad terms, Azure roles govern permissions for overseeing Azure resources, whereas Azure AD roles govern permissions for managing Azure AD resources.
The following table summarizes the Azure AD terminology:
|
Concept |
Description |
|
Identity |
An object that can be authenticated |
|
Account |
An identity that has data associated with it |
|
Azure AD account |
An identity created through Azure AD or another Microsoft cloud service |
|
Azure AD tenant/directory |
A dedicated and trusted instance of Azure AD, a tenant is automatically created when your organization signs up for a Microsoft cloud service subscription |
Azure AD is a crucial aspect of cloud security that enables organizations to control access to their resources and data in the cloud.
Securing applications with the Microsoft identity platform
Managing the information of multiple usernames and passwords across various applications can become challenging, time-consuming, and vulnerable to errors. However, this problem can be addressed using a centralized identity provider. Azure AD is one such identity provider that can handle authentication and authorization for various applications. It provides several benefits, including conditional access policies, MFA, and single sign-on (SSO). SSO is a significant advantage as it enables users to sign in once and automatically access all the applications that share the same centralized directory.
More broadly speaking, the Microsoft identity platform simplifies authentication and authorization for application developers. It offers identity as a service and supports various industry-standard protocols and open source libraries for different platforms. Developers can use this platform to build applications that sign in to all Microsoft identities, get tokens to call Microsoft Graph, and access other APIs. Simply put, by utilizing the Microsoft identity platform, developers can reduce the complexity of managing user identities and focus on building their applications’ features and functionality.
Microsoft’s identity platform can help organizations streamline identity management and improve security. Organizations can take advantage of features such as conditional access policies and MFA by delegating authentication and authorization responsibilities to a centralized provider such as Azure AD. Furthermore, developers can benefit from the platform’s ease of use, supporting various industry-standard protocols and open source libraries, making it easier to build and integrate applications.
By integrating your app with Azure AD, you can ensure that your app is secure in the enterprise by implementing Zero Trust principles.
As a developer, integrating your app with Azure AD provides a wide range of benefits that help you secure your app in the enterprise. One of the significant benefits of using Azure AD is the ability to authenticate and authorize applications and users. Azure AD provides a range of authentication methods, including SSO, which can be implemented using federation or password-based authentication. This simplifies the user experience by reducing the need for users to remember multiple passwords.
Another benefit of using Azure AD is the ability to implement RBAC, which enables you to restrict access to your app’s features based on a user’s role within the organization. You can also use OAuth authorization services to authenticate and authorize third-party apps that access your app’s resources.
The Microsoft identity platform supports multiple protocols for authentication and authorization. It is crucial to understand the differences between these protocols to choose the best option for your application.
One example is the comparison between OAuth 2.0 and SAML. OAuth 2.0 is commonly used for authorization, while SAML is frequently used for authentication. The OAuth 2.0 protocol allows users to grant access to their resources to a third-party application without giving the application their login credentials. On the other hand, SAML provides a way for a user to authenticate to multiple applications using a single set of credentials. An example of SAML being used in the Microsoft identity platform is with Active Directory Federation Services (AD FS) federated to Azure AD.
Another example is the comparison between OpenID Connect (OIDC) and SAML. OIDC is commonly used for cloud-based applications, such as mobile apps, websites, and web APIs. It allows for authentication and SSO using a JSON web token. SAML, on the other hand, is commonly used in enterprise applications that use identity providers such as AD FS federated to Azure AD. Both protocols support SSO, but SAML is commonly used in enterprise applications.
The following table summarizes the protocols and descriptions and their typical usage scenarios:
|
Protocol |
Description |
Use Cases |
|
OAuth |
OAuth is used for authorization, granting permissions to manage Azure resources |
When managing permissions to access and perform operations on Azure resources |
|
OIDC |
OIDC builds on top of OAuth 2.0 and is used for authentication, verifying the identity of users |
When authenticating users and obtaining information about their identity |
|
SAML |
SAML is used for authentication and is commonly used with identity providers, such as AD FS, to enable SSO in enterprise applications |
When integrating with enterprise applications and identity providers, particularly with AD FS federated to Azure AD |
Understanding these protocols and their differences can help you choose the best option for your application and ensure secure and efficient authentication and authorization.
As more companies transition their workloads to the cloud, they face the challenge of ensuring the security of their resources in these new environments. In order to effectively manage access to cloud-based workloads, organizations must establish definitive user identities and control access to data, while also ensuring authorized operations are performed. This is where Microsoft Entra comes in – which provides a set of multiple components that provide identity-based access control, permissions management, and identity governance to help organizations securely manage their cloud-based workloads.