I encounter far too many networks with policies in place that disable the built-in Windows Firewall with Advanced Security (WFAS) by default on all of their machines. Usually, if I ask about this, the reason is either unknown or It's always been that way. I think this is a carry-over from the Windows XP/Server 2003 days, or maybe even older, when the Windows Firewall was less than desirable. Believe me when I tell you that WFAS in today's operating systems is very advanced, stable, and beneficial. If you want to stop unnecessary or malicious traffic from getting to your server, look no further than this built-in tool.
Using Windows Firewall with Advanced Security to block unnecessary traffic
Getting ready
We are going to use two Windows Server 2016 machines for this task. We will test connectivity between the two to set our baseline and then create a rule that blocks the functions we just tested. Next, we will test again to ensure that our changes did what we expected them to, blocking the traffic that we attempt to generate. It is important to set up a baseline of tests and run those same tests following each change to ensure the rules are working exactly as you want them to.
How to do it...
If you want to stop unnecessary traffic from getting to your server, execute the following instructions:
- First, we want to test the existing connectivity. I log into my DC2 server, and from there I am able to successfully execute the ping web1 command and get a reply. I can also open up File Explorer and browse to \\WEB1 and see a folder shared there. This baseline test tells me that both ICMP (ping) traffic and file access are currently open and allowed by WFAS on WEB1. We want to stop these functions from happening.
- Log in to WEB1 and open Windows Firewall with Advanced Security. You can open this either from the Start screen and typing it in, or by opening a Run prompt and typing wf.msc.
- Inside WFAS, your two best friends when trying to control traffic are the Inbound Rules and Outbound Rules sections on the left. You need to think of Inbound and Outbound from the server's perspective. Inbound Rules manipulate traffic that is flowing in toward your server, and Outbound Rules handle traffic flowing out of your server toward the rest of the network. If you click on Inbound Rules, you will see the list of preconfigured rules that exist already.
- Right-click on Inbound Rules and click on New Rule....
- First, let's make a rule to block the file access from happening. Choose Port and on the next screen, enter the value for port TCP as 445. Then you realize that you might as well also block RDP access since that is also currently enabled. No problem! Simply comma separate these numbers as follows:
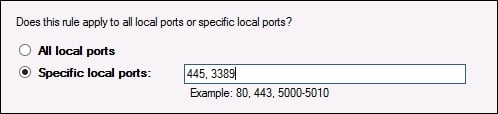
- Choose Block the connection.
- On the next screen where you choose which firewall profile the rule applies to, you can leave it set to all three checked as the default. This will ensure that the rule will apply to any NIC that has any firewall profile assigned. If you only have a single NIC on your server and it is joined to the domain, then you could get away with only selecting the domain profile if you wanted to deselect the other two. For our recipe, I'm going to leave them all checked.
- Type any kind of descriptive name for your rule—something like Block File and RDP Access.
- You did it! You will see that the new rule exists, and it is immediately put into action. If you head over to your other server, you will now find that you can no longer RDP or browse the file shares at all on WEB1.
- We can still successfully ping WEB1, though, and we wanted to put a stop to that as well. To stop ICMP traffic, you simply need to create another rule. This one is a little bit more complicated, though. First, go ahead and create a second Inbound Rule, and use the exact same settings that you used for your RDP file rule. You can enter anything into the Port field; it doesn't matter because we will be invalidating it in a minute, so maybe use port 445 for our example.
- Great, now you have two rules in there that are both blocking port 445. That doesn't do us much good. Right-click on the newest rule that we just created, head into Properties, and let's improve this rule a little bit.
- Inside the Protocols and Ports tab, drop down the Protocol type and choose ICMPv4. That's all you have to do! You have now modified this rule so that it is no longer blocking TCP port 445, but rather this rule is now blocking ICMPv4 traffic:
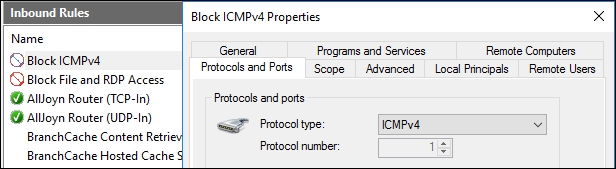
- If you log back into DC2, we no longer receive ping replies when trying to contact the WEB1 server.
Take some time to play around inside the Scope tab. This section of a WFAS rule allows you to scope the rule down so that it only applies to particular IP addresses or ranges. Maybe you only want to block file share access from a particular subnet or only for the external NIC of an edge server. Requirements like these are easy to accomplish!
How it works...
We used the Windows Firewall with Advanced Security to create a couple of simple rules to block unwanted traffic coming into our server. These rules are put into place immediately and are very easy to generate. What is even greater is that our WFAS rules can be created centrally by making use of Group Policy so that you don't even have to touch the individual servers to apply connection rules to them. WFAS is very different than the Windows Firewall of 10 years ago, and if you are not making use of it today I seriously recommend that you reconsider.



























































