This recipe will cover the installation of a DPM agent from the DPM console as well as a manual-based installation.
Installing the DPM agents
Getting ready
Before you can start protecting a workload within your datacenter, you must install a DPM agent on the server hosting the workload that you would like to protect (that is, Hyper-V, SQL Server, Exchange, and so on).
You can install the DPM agent via the DPM Administrator Console in push mode; however, there are some scenarios where you will not able to perform a push installation of the DPM agent to the server hosting the workload that you would like to protect. On the DPM server, you can find two executables for the DPM agent that you can share or download to a removable media. Then, you can install the agent manually. The DPM agent is also available on the DPM installation media. There are two different executables here:
- DpmAgentInstaller_x86.exe is for 32-bit operating systems
- DpmAgentInstaller_x64.exe is for 64-bit operating systems
Both are applicable for Windows server and Windows client operating systems.
How to do it...
The following steps will illustrate the process of installing DPM agent in two different ways.
Option 1 – installing the agent from the DPM console
- Open the DPM Administrator Console and click Management | Agents. Click Install on the tool ribbon to open the Protection Agent Installation Wizard.
- On the Select Agent Deployment Method page, click Install agents | Next.
- On the Select Computers page, DPM will display a list of available computers that are in the same domain as the DPM server. Add the required computer.
- The Advanced button page is enabled only when there is more than one version of a protection agent available for installation on the computers. You can use this option to install a previous version of the protection agent that was installed before you upgraded DPM server to a more recent version. However, it's recommended that you always keep the protection agent updated.
- Click Next > to continue.
- On the Enter Credentials page, type the username and password for a domain account that is a member of the local administrators group on the selected computer(s).
- If you select a node in a cluster, DPM detects all of the additional nodes in the cluster and displays the Select Cluster Nodes page. On the Select Cluster Nodes page, select an option that you want DPM to use for installing agents on additional nodes in the cluster. Then, click Next.
- In the Choose Restart Method step, select the method that you want to use to restart the selected computers after the protection agent has been installed.
- If any of the computers that you have selected are members of a cluster, an additional Choose Restart Method page will appear that you can use so that you can select the method to restart the clustered computers.
- Choose an appropriate option and click on Next > to continue.
- In the Summary page, you can verify the information you have chosen and then click on Install to initialize the installation and configuration process of the DPM agent.
- After a short period of time, the Agent will appear in the DPM console and report back with status OK.
Option 2 – installing the agent manually
You can perform a manual installation in two different ways:
- By providing the FQDN of the DPM server when running the DpmAgentInstaller executable
- By providing the NetBIOS name of the DPM server using setdpmserver.exe if the DPM agent is already installed but not configured
Now follow these steps:
- On the computer that you want to protect, open an elevated command window, and then run net use Z: \\<DPMServerName>\d$, where Z is the local drive letter that you want to assign and <DPMServerName> is the name of the DPM server that will protect the computer. d$ is where DPM software is installed.
- For a 64-bit computer, type the following:
cd /d <assigned drive letter>:\Program Files\Microsoft System Center 2019\DPM\DPM\ProtectionAgents\RA\5.0.<build number>.0\amd64
Here, <assigned drive letter> is the drive letter that you assigned in the previous step and <build number> is the latest DPM build number. For example:
cd /d "Z:\Program Files\Microsoft System Center 2019\DPM\DPM\ProtectionAgents\RA\5.0.158.0\amd64"
-
For a 32-bit computer, type the following:
cd /d <assigned drive letter>:\Program Files\Microsoft System Center 2019\DPM\DPM\ProtectionAgents\RA\5.0.<build number>.0\i386
Here, <assigned drive letter> is the drive that you mapped in the previous step and <build number> is the latest DPM build number.
-
To install the protection agent for a 64-bit computer, run the following command:
DPMAgentInstaller_x64.exe <DPMServerName>
Here, <DPMServerName> is the fully qualified domain name (FQDN) of the DPM server.
- To install the protection agent for a 32-bit computer, run the following command:
DPMAgentInstaller_x86.exe <DPMServerName>
Here, <DPMServerName> is the FQDN of the DPM server.
- Select I accept the license terms and conditions for the Microsoft Software License Terms, and click OK.
- The installation will start and you will receive a confirmation message that states Agent installation completed successfully. The DPM agent has now been configured and the appropriate firewall exceptions have been made in the domain profile of the Windows Firewall. Press Enter key to close the window.
- If the DPM agent is already installed, you should run the setdpmserver.exe executable with the –dpmservername switch to configure the DPM server that the DPM agent should report to as follows:
Setdpmserver –dpmservername DPM2019
After installing the agent manually, you must attach the DPM agent to the DPM server. You can do this via the DPM Administrator console or via the DPM PowerShell cmdlet.
- Open the DPM console and go to Management. Click on Production Servers and, at the top-left corner of the console, click on the Add button to start the Production Server Addition Wizard.
- Under the Select Agent Deployment Method page, click Attach agents, followed by Computer on trusted domain. Click the Next > button to continue:
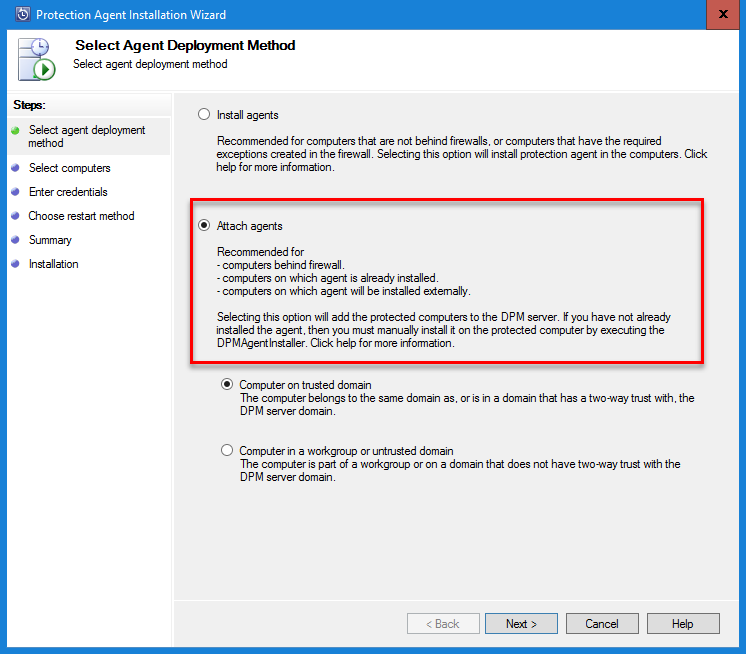
- In the Select Computers page, choose the server that you would like to attach to the DPM server and click on Next > to continue.
- In the Enter Credentials page, enter the credentials that should be used to execute this process. Keep in mind that the credentials you provide must have administrative rights on the server that you are trying to attach. Provide the credentials and click on Next > to continue.
- In the Summary page, verify the configuration and click on Attach to start.
- Verify that the Attach protected computer task has been successful. Click Close to close the Protection Agent Installation Wizard.
- The Agent will appear in the DPM console and report back with status OK.
How it works...
The DPM agent is the core component for the DPM so that it's able to provide restore capabilities for your data. The DPM relies on the DCOM object of the protected server which is mapped to the DPMRA service so that the SQL job on the DPM server starts. System Center Data Protection Manager stores all protection group configurations as SQL Jobs, and the SQL Server Agent initializes the DPM agent to start creating snapshots by using the underlying architecture of the Volume Shadow Copy Service (also known as Volume Snapshot Service or VSS) within the operating system.
The setdpmserver.exe executable command has the ability to configure the DPM agent to set which DPM server the DPM agent reports to. It also provides the configuration needed for the local Windows Firewall so that the DPM agent can start reporting to the DPM server.
There's more...
System Center Data Protection Manager manages data replication and provides management of the DPM agents using two different TCP ports:
- 5718
- 5719
TCP port 5718 is used for data replication and TCP port 5719 is used by the DPM agent coordinator. The coordinator is the function within the DPM agent architecture that manages the installation, uninstallation, and updates of the DPM agent. For more information regarding firewall ports and configuration, please read the Planning your DPM deployment recipe in this chapter.




























































