Now that we are clear with the shared security responsibilities model, let us deep dive into the resources provided by AWS to secure your AWS account and resources inside your AWS account from unauthorized use. AWS gives you a host of tools for securing your account such as MFA, several options for credentials that can be used to access AWS services and accounts for multiple use cases, secure endpoints to communicate with AWS services, centralized logging service for collecting, storing and analyzing logs generated for all user activities in your AWS account by your resources in your AWS account and logs from all your applications running in your AWS account. Along with these features, you also have AWS Trusted Advisor that performs security checks for all AWS services in your AWS account. All of these tools are generic in nature and they are not tied to any specific service; they can be used with multiple services.
AWS account security features
AWS account
This is the account that you create when you first sign up for AWS. It is also known as a root account in AWS terminology. This root account has a username as your email address and password that you use with this username. These credentials are used to log into your AWS account through the AWS Management Console, a web application to manage your AWS resources. This root account has administrator access for all AWS services, hence AWS does not recommend using root account credentials for day-to-day interactions with AWS; instead, they recommend creating another user with the required privileges to perform those activities. In some cases, your organization might decide to use multiple AWS accounts, one for each department or entity for example, and then create IAM users within each of the AWS accounts for the appropriate people and resources.
Let us look at the following scenarios for choosing strategies for AWS account creation:
|
Business requirement |
Proposed design |
Comments |
|
Centralized security management |
One AWS account |
Centralizes information security management and minimal overhead. |
|
Separation of production, development, and testing environments |
Three AWS accounts |
One account each for production, development, and the testing environment. |
|
Multiple autonomous departments |
Multiple AWS accounts |
One account each for every autonomous department of organization. Assigns access control and permissions for every single account. Benefits from economies of scale. |
|
Centralized security management withmultiple autonomous independent projects |
Multiple AWS accounts |
Creates one AWS account for shared project resources such as Domain Name Service, User Database, and so on. Create one AWS account for each autonomous independent project and grant them permissions at granular level. |
Having multiple AWS accounts also helps in decreasing your blast radius and reducing your disaster recovery time. So if there is something wrong with one AWS account, the impact will be minimal on running business operations, as other accounts will be working as usual along with their resources. Having multiple AWS accounts also increases security by segregating your resources across accounts based on the principle of least privilege.
AWS credentials
AWS uses several types of credentials for authentication and authorization as follows:
- Passwords
- Multi-factor authentication
- Access keys
- Key pairs
- X.509 certificates
We will have a detailed look at these credentials in Chapter 2, AWS Identity and Access Management.
Individual user accounts
AWS provides a centralized web service called AWS IAM for creating and managing individual users within your AWS Account. These users are global entities. They can access their AWS account through the command line interface (CLI), through SDK or API, or through the management console using their credentials. We are going to have a detailed look at IAM in the next chapter.
Secure HTTPS access points
AWS provides API endpoints as a mechanism to securely communicate with their services; for example, https://dynamodb.us-east-1.amazonaws.com is an API endpoint for AWS DynamoDB (AWS NoSQL service) for us-east-1 (Northern Virginia) region. These API endpoints are URLs that are entry points for an AWS web service. API endpoints are secure customer access points to employ secure HTTPS communication sessions for enabling better security while communicating with AWS services. HTTPS uses Secure Socket Layer (SSL) / Transport Layer Security (TLS) cryptographic protocol that helps prevent forgery, tampering and eavesdropping. The identity of communication parties is authenticated using public key cryptography.
Security logs
Logging is one of the most important security feature of AWS. It helps with auditing, governance and compliance in cloud. AWS provides you with AWS CloudTrail that logs all events within your account, along with the source of that event at 5 minute interval, once it is enabled. It provides you with information such as the source of the request, the AWS service, and all actions performed for a particular event.
AWS CloudTrail logs all API calls such as calls made through AWS CLI, calls made programmatically, or clicks and sign-in events for the AWS Management Console.
AWS CloudTrail will store events information in the form of logs; these logs can be configured to collect data from multiple regions and/or multiple AWS accounts and can be stored securely in one S3 bucket. Moreover, these events can be sent to CloudWatch logs and these logs could be consumed by any log analysis and management tools such as Splunk, ELK, and so on.
Amazon CloudWatch is a monitoring service that has a feature CloudWatch log that can be used to store your server, application and custom log files and monitor them. These log files could be generated from your EC2 instances or other sources such as batch processing applications.
We are going to have a detailed look at the logging feature in AWS along with AWS CloudTrail and Amazon CloudWatch in the subsequent chapters.
AWS Trusted Advisor security checks
The AWS Trusted Advisor customer support service provides best practices or checks across the following four categories:
- Cost optimization
- Fault tolerance
- Security
- Performance
Let us look at alerts provided by the AWS Trusted Advisor for security categories. If there are ports open for your servers in cloud, that opens up possibilities of unauthorized access or hacking; if there are internal users without IAM accounts, or S3 buckets in your account are accessible to the public, or if AWS CloudTrail is not turned on for logging all API requests or if MFA is not enabled on your AWS root account, then AWS Trusted Advisor will raise an alert. AWS Trusted Advisor can also be configured to send you an email every week automatically for all your security alert checks.
The AWS Trusted Advisor service provides checks for four categories; these is, cost optimization, performance, fault tolerance, and security for free of cost to all users, including the following three important security checks:
- Specific ports unrestricted
- IAM use
- MFA on root account
There are many more checks available for each category, and these are available when you sign up for the business or enterprise level AWS support. Some of these checks are as follows:
- Security groups-Unrestricted access
- Amazon S3 bucket permissions
- AWS CloudTrail logging
- Exposed access keys
The following figure depicts the AWS Trusted Advisor checks for an AWS account. We will take a deep dive into the Trusted Advisor security checks later in this book:

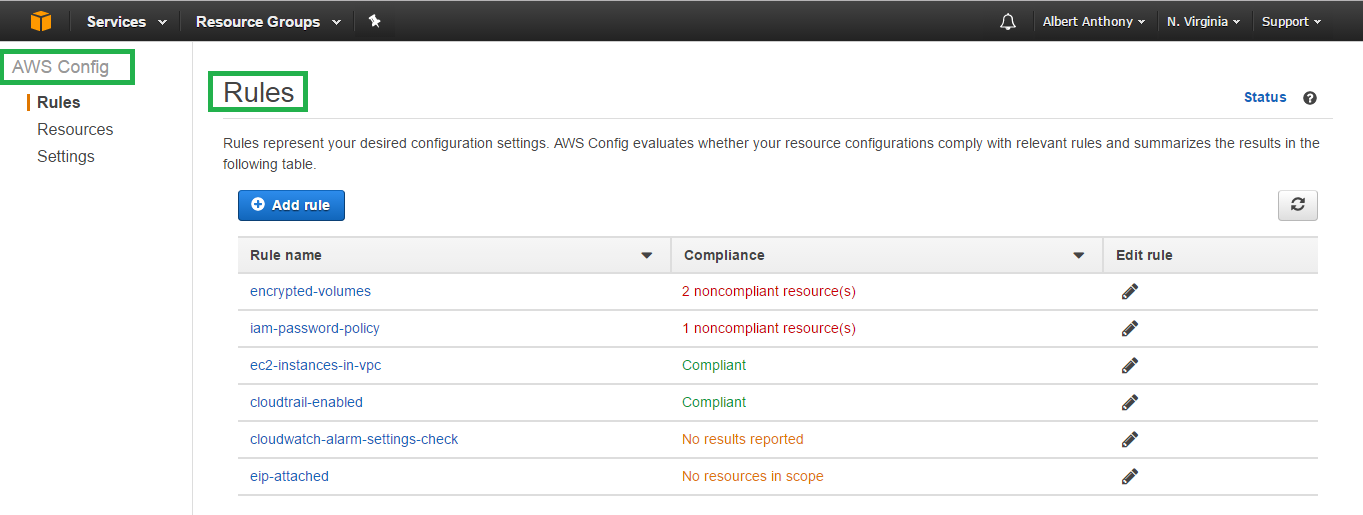
AWS Config security checks
AWS Config is a continuous monitoring and assessment service that records changes in the configuration of your AWS resources. You can view the current and past configurations of a resource and use this information to troubleshoot outages, conduct security attack analysis, and much more. You can view the configuration at time and use that information to reconfigure your resources and bring them into a steady state during an outage situation.
Using Config Rules, you can run continuous assessment checks on your resources to verify that they comply with your own security policies, industry best practices, and compliance regimes such as PCI/HIPAA. For example, AWS Config provides managed Config rules to ensure that encryption is turned on for all EBS volumes in your account. You can also write a custom Config rule to essentially codify your own corporate security policies. AWS Config send you alerts in real time when a resource is wrongly configured, or when a resource violates a particular security policy.
The following figure depicts various rule sets in AWS Config; these could be custom rules or rules provided out of the box by AWS: