Authentication methods in Azure AD
Several approaches can be leveraged to authenticate your users to Azure AD. In this section, you will explore these methods and understand their use cases.
The authentication security methods available in Microsoft 365 are as follows:
- Multi-factor authentication (MFA)
- Self-service password reset (SSPR)
- Conditional Access
- Passwordless
The following sections will briefly introduce the principles of these methods; however, each of these will be explored in greater detail in Chapter 2, Authentication and Security, and Chapter 3, Implementing Conditional Access Policies.
Multi-factor authentication
MFA in Azure AD provides two-step verification for Microsoft services via a combination of approved authentication methods determined by Microsoft 365 administrators. The available methods can be based on the following:
- Something you know, such as your password
- Something you own, such as your mobile phone or an OAuth hardware token
- Something you are, such as biometric identification (fingerprint or facial recognition)
When setting up MFA for users in your Microsoft 365 environment, users must first complete a registration process to provide information about themselves to Azure AD and set their authentication method preferences.
Once set, users will be challenged with an MFA prompt when accessing Microsoft 365 services and applications using their Azure AD credentials, as shown in the following diagram:
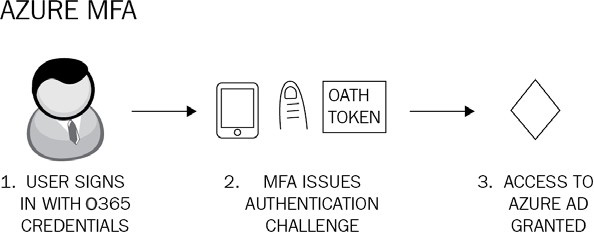
Figure 1.2: Azure MFA
MFA can also be configured to work in conjunction with Conditional Access, with trusted locations that you define by entering the IP ranges of your business operating units so that users will not be issued an MFA challenge when working in these locations. Conditional Access with MFA also enables you to apply another layer of security by ensuring that any access requests to specific apps and resources can be secured and protected, by requiring the requesting user to complete an MFA challenge before being granted the access they require.
Note
It is recommended that you configure MFA for all privileged user accounts within your Microsoft 365 environment, except for your permanent break-glass accounts, which should be cloud-only accounts with the domain suffix of the .onmicrosoft.com domain name. Alternative authentication protection should be applied to these break-glass accounts. Break-glass accounts will be covered in more detail in Chapter 3, Implementing Conditional Access Policies.
Self-service password reset
Whilst not strictly an authentication method in itself, SSPR is a user feature designed to remove the requirement of IT staff to respond to user requests to reset their passwords in Azure AD. An initial registration process is required at https://aka.ms/SSPRSetup for each user to set up SSPR, during which time they must provide authentication methods to verify their identity.
Note
To reset the password, the user visits https://passwordreset.microsoftonline.com.
SSPR can be used for both cloud-only and hybrid identity users. If the user is cloud-only, then their password is always stored encrypted in Azure AD, whereas hybrid users have their password written back to on-premises AD. This is achieved using a feature that can be enabled in Azure AD Connect called password writeback.
The basic principles of SSPR are illustrated in the following diagram:
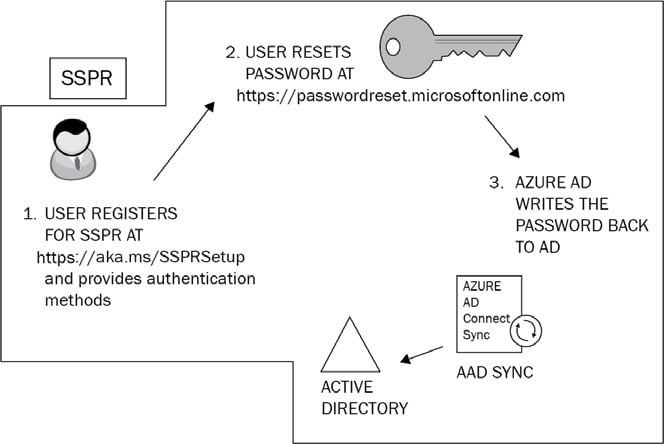
Figure 1.3: Self-service password reset
The process of registering your users for SSPR is now combined with that of the MFA registration process. Previously, there were two separate registration processes for these technologies.
When SSPR is enabled on your Azure AD environment, you can assist your users by configuring notifications that make them aware when their passwords have been reset. You can also increase security by setting administrator notifications to monitor and alert whenever an administrator changes a password. It is also possible to customize a helpdesk email or URL to provide immediate guidance to users who experience problems when attempting to reset their passwords.
Note
When using SSPR with password writeback for your hybrid identities, you will require Azure AD Premium P1 licenses.
Conditional Access
Conditional Access is a powerful feature of Azure AD Premium P1 that allows Microsoft 365 administrators to control access to applications and resources within your organization. With Conditional Access, you can automate the process of controlling the level of access that users will have to these applications and resources by setting Conditional Access policies. Azure AD will then make decisions on whether to grant or deny access based on the conditions that you set in these policies. The basic principles are shown in the following diagram:
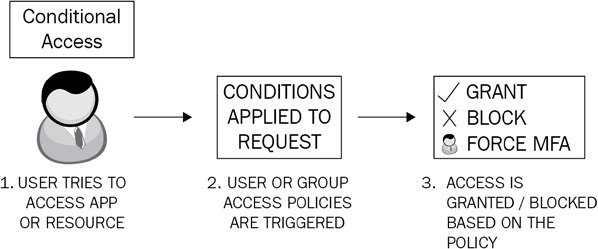
Figure 1.4: Conditional Access
While it is possible to apply some default security settings to your Microsoft 365 environment with security defaults (auto-applied on newer tenants), you will undoubtedly need to plan and define custom policies with specific conditions and exceptions. For example, you would not wish to force MFA on your permanent break-glass global administrator account. We will examine Conditional Access in greater detail in Chapter 3, Implementing Conditional Access Policies.
Note
Conditional Access settings frequently require some additional features of Azure AD to be configured, for example, Azure AD Identity Protection. This will have an impact on your decision-making process as it relates to licensing. While Conditional Access is a feature of Azure AD Premium P1, the use of Azure AD Identity Protection features would necessitate Azure AD Premium P2 licenses.
Passwordless authentication
Passwords are more vulnerable than ever before and can be exploited and compromised by malicious actors using techniques such as phishing, spray attacks, and social engineering attacks. Switching to a passwordless authentication method helps mitigate such risks.
Microsoft provides three types of passwordless authentication for Azure AD. These are as follows:
- Microsoft Authenticator: Can enable iOS or Android phones to be used as passwordless credentials by providing numerical challenges.
- FIDO2-compliant security keys: Hardware keys provided by a number of third-party manufacturers; ideal for highly privileged identities or shared machines in kiosks.
- Windows Hello for Business: Available on Windows computers and ideal for users with their own designated Windows device. Biometric and PIN credentials are directly configured on the device to prevent access from anyone but the authorized user.
Note
Links to further resources on Microsoft Authenticator, FIDO2-compliant security keys, and Windows Hello for Business can be found in the Further reading section at the end of this chapter.
Now that you understand the available authentication methods, let’s explore the directory synchronization methods supported by Azure AD Connect.
























































