Before mingling with Metasploit, we need to have a test lab. The best idea for establishing a test lab is to gather different machines and install different operating systems on them. However, if we only have a single computer, the best idea is to set up a virtual environment.
Virtualization plays a major role in penetration testing today. Due to the high cost of hardware, virtualization plays a cost-effective role in penetration testing. Emulating different operating systems under the host operating system not only saves you cost but also cuts down on electricity and space. Setting up a virtual penetration test lab prevents any modifications on the actual host system and allows us to perform operations in an isolated environment. A virtual network allows network exploitation to run on an isolated network, thus preventing any modifications or the use of network hardware of the host system.
Moreover, the snapshot feature of virtualization helps preserve the state of the virtual machine at a particular interval of time. Hence, snapshots prove to be very helpful, as we can compare or reload a previous state of the operating system while testing a virtual environment without reinstalling the entire software in case the files modify after attack simulation.
Virtualization expects the host system to have enough hardware resources, such as RAM, processing capabilities, drive space, and so on, to run smoothly.
So, let us see how we can create a virtual environment with the Kali operating system (the most favored OS for penetration testing, which contains Metasploit Framework by default).
To create virtual environments, we need virtual emulator software. We can use either of the two most popular ones, VirtualBox and VMware Player. So, let us begin the installation by performing the following steps:
- Download VirtualBox (http://www.virtualbox.org/wiki/Downloads) and set it up according to your machine's architecture.
- Run the setup and finalize the installation.
- Now, after the installation, run the VirtualBox program as shown in the following screenshot:
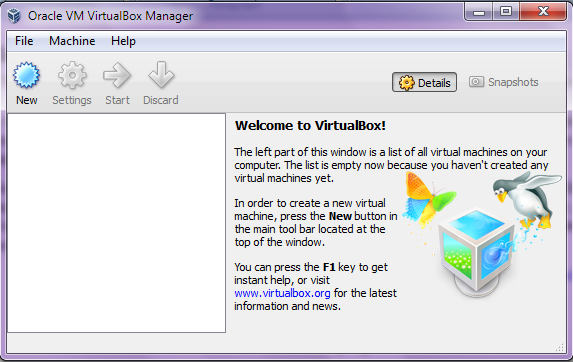
- Now, to install a new operating system, select New.
- Type an appropriate name in the Name field and choose the operating system Type and Version, as follows:
- For Kali Linux, select Type as Linux and Version as Linux 2.6/3.x/4.x(64-bit) based on your system's architecture
- This may look something similar to what is shown in the following screenshot:
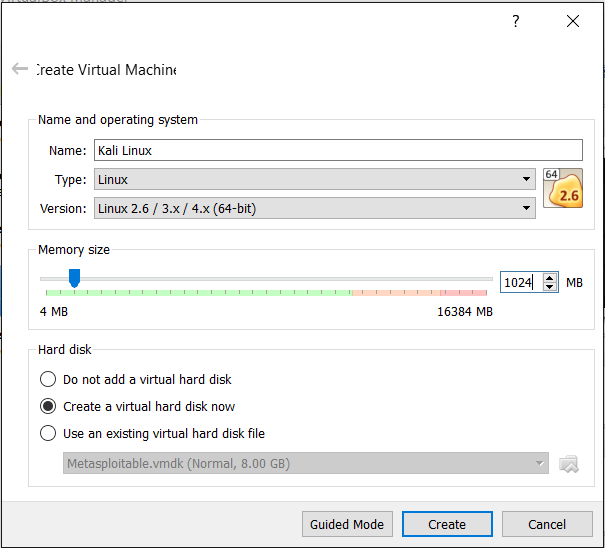
- Select the amount of system memory to allocate, typically 1 GB for Kali Linux.
- The next step is to create a virtual disk that will serve as a hard drive to the virtual operating system. Create the disk as a dynamically allocated disk. Choosing this option will consume just enough space to fit the virtual operating system, rather than consuming the entire chunk of physical hard disk of the host system.
- The next step is to allocate the size for the disk; typically, 20-30 GB space is enough.
- Now, proceed to create the disk and, after reviewing the summary, click on Create.
- Now, click on Start to run. For the very first time, a window will pop up showing the selection process for a startup disk. Proceed with it by clicking Start after browsing the system path for Kali OS's .iso file from the hard drive. This process may look similar to what is shown in the following screenshot:
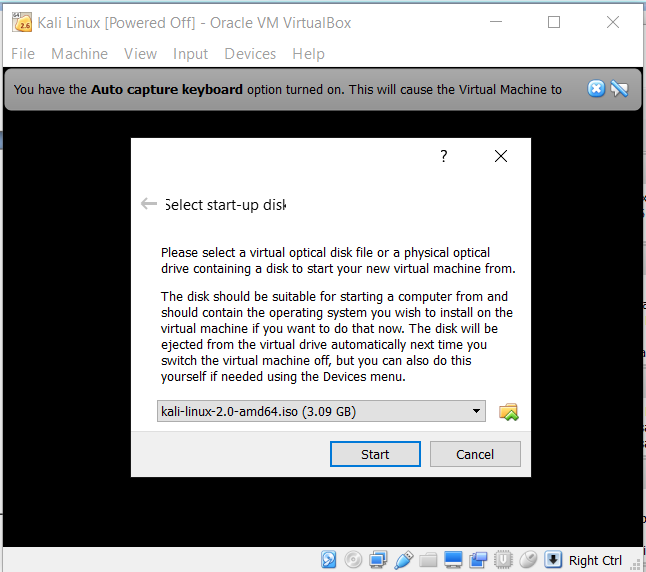
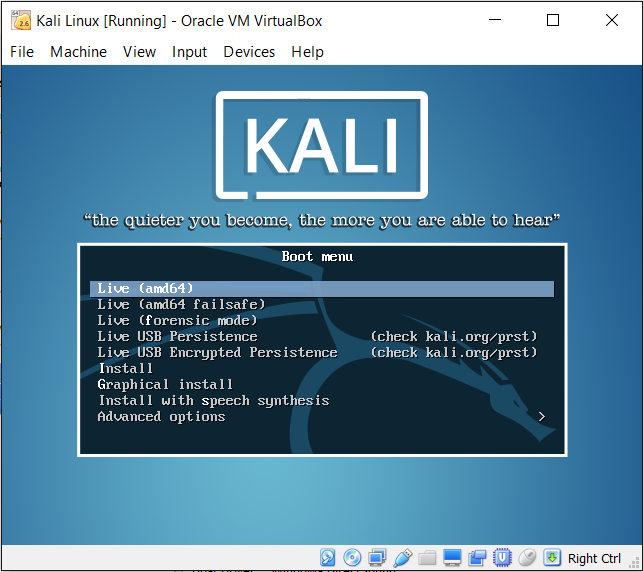
You can run Kali Linux in a Live mode, or you can opt for Graphical install to install it persistently, as shown in the following screenshot:
For installing Metasploit on Windows, refer to an excellent guide at https://community.rapid7.com/servlet/JiveServlet/downloadBody/2099-102-11-6553/windows-installation-guide.pdf.




























































