Physical and virtual network and security devices
For the certification exam, it is important that you understand the strengths and weaknesses of all the proposed network devices/appliances, the correct placement of network devices for maximum effect, and the required security configuration.
OSI model
No introduction to networking would be complete without a brief introduction to the Open Systems Interconnection (OSI) 7-layer model. As we move through the chapters, you will occasionally see references to layers. This has become a standard reference model and it allows for different vendors to implement services, protocols, and hardware using this reference model. Throughout the book, we will discuss applications, services, protocols, and appliances that sit at different layers within the model. Although the CompTIA Advanced Security Professional 004 (CASP 004) exam will not be testing your knowledge specifically (OSI is not a listed objective), it can be useful as a reference aid when we discuss networking subjects. The model is not actually defining a complete working network model—it is a conceptual model. For example, to fully understand the details of the Simple Mail Transport Protocol (SMTP), you would need to gain access to Internet Engineering Task Force (IETF) Request for Comments (RFC) documents. Imagine you are looking to manufacture network cables to meet Category 6 (CAT 6) standards—you could access International Organization for Standardization/International Electrotechnical Commission (ISO/IEC 11801) standards documentation. See the following screenshot for an overview of the OSI 7-layer model:
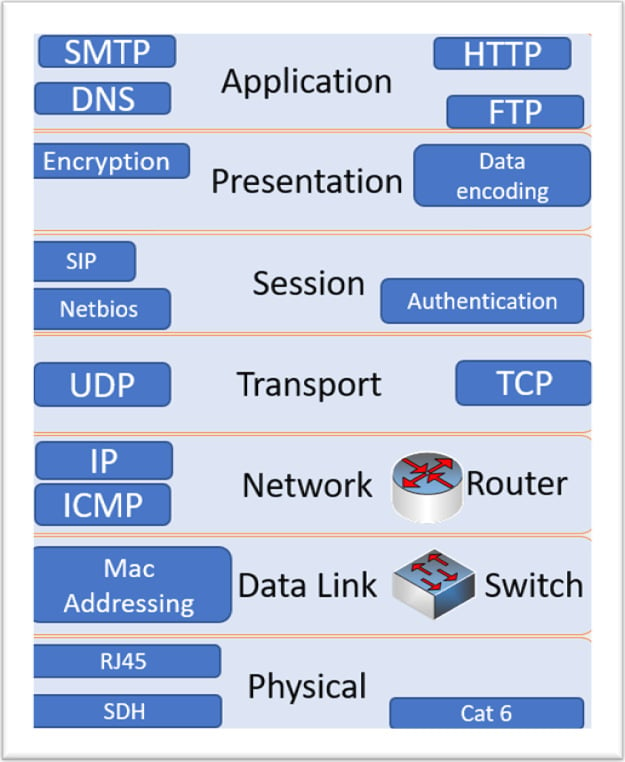
Figure 1.1 – OSI 7-layer model
Vulnerabilities may exist across multiple layers within the OSI model. For example, we may be vulnerable to Man-in-the-Middle (MITM) attacks on our layer 2 switch. We will take a look at the many different threats that may impact an enterprise network throughout the book.
Unified threat management
A unified threat management (UTM) appliance offers firewall functionality and many additional security functions; it is deployed as a single security appliance or software solution. This security solution offers a comprehensive suite of security features all in a single package. While this is a good solution for small enterprises with limited resources (limited staff and limited budget), it does not offer the DiD required by enterprise customers.
UTMs may include a significant number of converged security features, but not necessarily all of the following:
- Network firewall
- Intrusion detection system (IDS)
- Intrusion prevention system (IPS)
- Deep packet inspection (DPI)
- Data loss prevention (DLP)
- Anti-virus capability
- Web application firewall (WAF)
- Web proxy and content filtering
- Spam filtering
- Security information and event management (SIEM)
The following screenshot shows the combined security features supported on a UTM appliance:
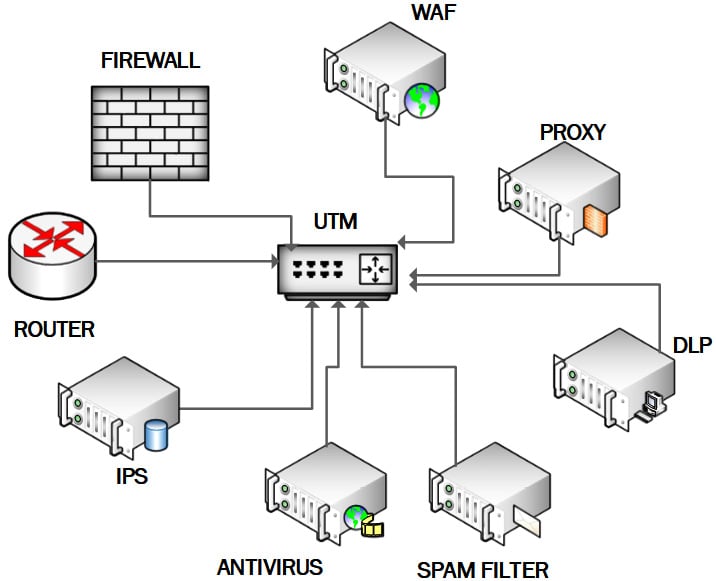
Figure 1.2 – UTM appliance
Advantages
UTM has the following advantages:
- Reduction in management actions (compare the scenario of a small information technology (IT) security team managing and monitoring multiple security appliances)
- Reduced footprint in the data center (less hardware)
- Less cost
Disadvantages
UTM has the following disadvantages.
- Risk from a single point of failure (SPOF) (limited hardware resources are providing many services)
- Negative performance impact on a network due to the workload handled by the device
IDS/IPS
Intrusion detection is an essential security function, typically implemented on the perimeter to protect your organization from incoming threats. It will alert the security team to inbound threats.
Intrusion prevention is the process of performing intrusion detection and then stopping detected incidents. These security measures are available as IDS and IPS. Active protection is the more commonly adopted approach, meaning a network intrusion prevention system (NIPS) will be seen protecting most enterprise networks.
IDS and IPS constantly watch your network, identifying possible incidents and logging information about them, stopping incidents, and reporting them to security administrators. In addition, some networks use IDS/IPS for identifying problems with security policies and deterring individuals from violating security policies. IDS/IPS have become a necessary addition to the security infrastructure of most organizations, precisely because they can stop attackers while they are gathering information about your network.
Examples of intrusions
Indicators of compromise (IOCs) can be unusual traffic, attacks against protocols (such as high volumes of Internet Control Message Protocol (ICMP) traffic), and malicious payloads. The result could be excess traffic causing denial of service (DoS) or compromised systems through unwanted deployments of Trojans and backdoors.
There are two main IDS detection techniques that are routinely used to detect incidents, as outlined here:
- Signature-based detection compares known signatures against network events to identify possible incidents. This is regarded as the simplest detection technique as it evaluates attacks based on a database of signatures written by the vendor or operator. In the same way as a first-generation firewall, this approach is limited as it is based on known patterns.
Examples:
A Secure Shell (SSH) connection using the root account would be in the ruleset.
An email with the subject password reset and an attachment with the name passregen.exe would be identified as malicious.
- Anomaly-based detection compares definitions of what is considered a normal/benign activity with observed events to identify significant deviations. This detection method can be very effective at spotting previously unknown threats. This type of detection is also known as heuristics-based detection.
Example:
The SMTP messaging server usually contributes to 23% of traffic on the network. If the SMTP server is suddenly generating 70% of the network traffic, this would generate alerts.
Network IDS versus NIPS
The NIPS sits directly behind the firewall (inline) and traffic needs to be forwarded onto the network. The NIPS can block unwanted traffic and payloads. This is illustrated in the following diagram:
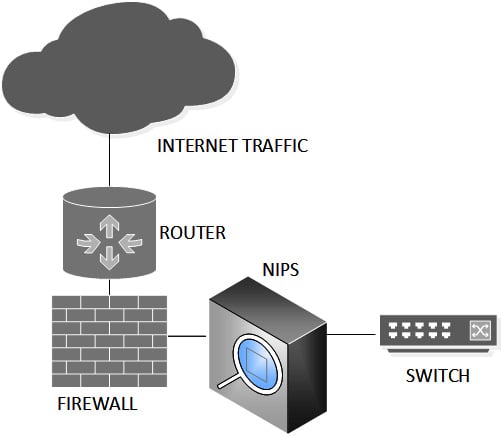
Figure 1.3 – NIPS placement (inline)
Network IDS (NIDS) does not need to be inline; it can monitor traffic but will need to use port mirroring or spanning on the network switch to be effective, as illustrated in the following diagram:
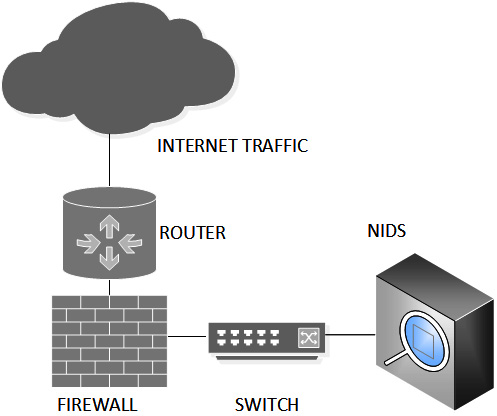
Figure 1.4 – NIDS placement
Wireless IPS
In addition to fixed or wired networks, many organizations may need the flexibility of a Wi-Fi network.
A wireless IPS (WIPS) is designed to detect the use of rogue or misconfigured wireless devices. A rogue device can spoof media access control (MAC) addresses of trusted network devices. A WIPS can build up a database of known trusted hosts on the network and can also be used to prevent DoS attacks.
An effective WIPS should mitigate the following types of threats:
- Ad hoc networks: These use peer-to-peer (P2P) connections to evade security controls and risk exposure to malware.
- Rogue access points (APs): These allow attackers to bypass perimeter security.
- Evil-twin APs: Users may connect to this lookalike network and be vulnerable to sniffing.
- Misconfigured APs: These expose a network to possible attacks due to configuration errors.
- Client misassociation: This risks infection from connecting to other service set identifiers (SSIDs) while in range of the authorized AP.
- MITM attack: An attacker will route traffic through their network device and sniff the traffic.
- MAC spoofing: This may allow the attacker to bypass access-control lists (ACLs) on the AP or allow them to impersonate another network device.
- DoS attack: This happens when a continuous stream of fake requests or messages is sent to the AP.
Inline encryptors
The High Assurance Internet Protocol Encryptor Interoperability Specification (HAIPE-IS) requires inline network encryption (INE) devices to be interoperable. For example, Tactical Local Area Network Encryptor (TACLANE) is a product used by the United States (US) government and the Department of Defense (DOD); it is military-grade and meets National Security Agency (NSA) security requirements. It is manufactured by General Dynamics. This is a device that enables encrypted communication over untrusted networks. Commercial organizations will use site-to-site virtual private network (VPN) links and not need this technology. The following figure shows a TACLANE INE device:

Figure 1.5 – INE device
This device meets the high assurance required by government and military remote connections.
Network access control
Network access control (NAC) enforces a strong, secure posture for devices that connect to our enterprise networks.
A major challenge for many enterprise networks is unmanaged bring your own device (BYOD) devices and guest devices accessing wireless and switched networks. The goal is to control access to the network, ensuring devices are compliant with baseline security policy. You would want to ensure devices had anti-virus installed and had security patches and firewall functionality.
Devices typically connect through a registration virtual local area network (VLAN) using a captive portal. If devices are found to be compliant, they could gain network access. Devices found to be uncompliant would be routed through to an isolation VLAN, able to access remediation services. The following diagram shows the components of NAC:
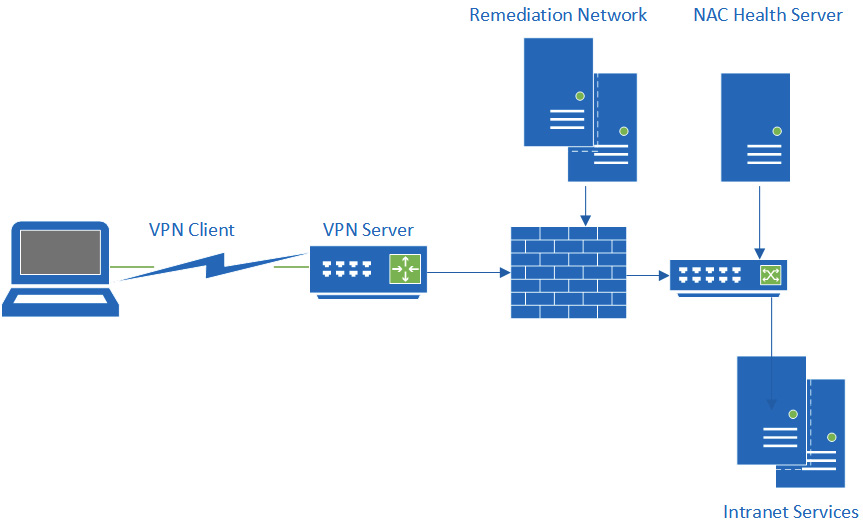
Figure 1.6 – NAC
PacketFence offers a free and open source NAC solution that is distributed under the General Public License (GPL). The software can be accessed via https://www.packetfence.org/.
SIEM
SIEM allows an organization to centralize security management events, forwarding logs from security appliances to a central system. It provides correlation and normalization for context and alerting, and also provides reporting and alerts based upon real-time logged data inputs. The following diagram shows the architecture of centralized SIEM:

Figure 1.7 – SIEM architecture
Advanced solutions can use behavioral analytics to detect anomalous user behaviors. Privileged user monitoring is a common requirement for compliance reporting. The following screenshot shows a SIEM dashboard:
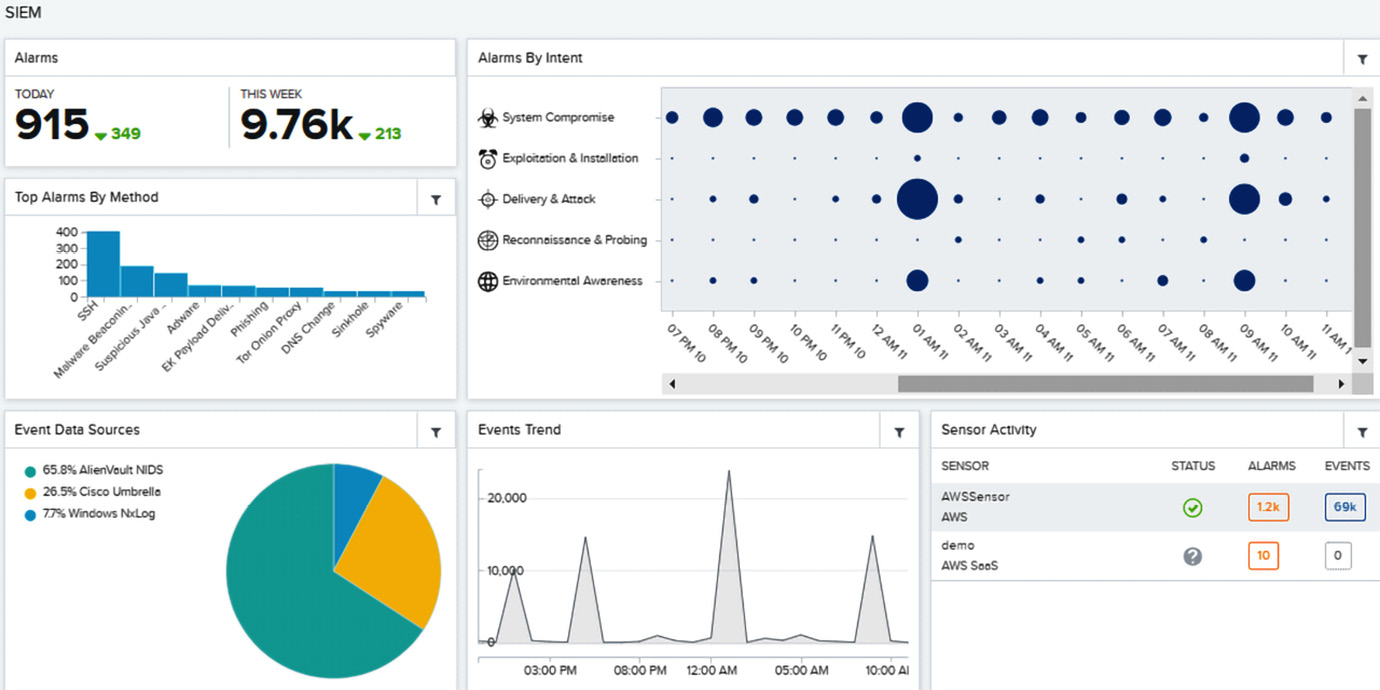
Figure 1.8 – AlienVault/AT&T SIEM dashboard
SIEM threat intelligence can help security operations center (SOC) teams pinpoint malicious or risk-based events and deliver a response. Analytics and machine learning (ML) are used to produce insights from huge amounts of collated data; they offer automation to identify hidden threats. Benefits include the following:
- Real-time monitoring: Stop threats that can be fast-moving.
- Incident response: Quickly identify threats to begin a response.
- User monitoring: This will identify unusual user behaviors and risky privilege use.
- Threat intelligence: Build up knowledge of security teams.
- Advanced analytics: Aid the analysis of large amounts of logged data.
- Advanced threat detection : SOC analysts need this advanced toolset to detect and address IOCs.
Switches
A switch is a network device that connects devices on a computer network by receiving and forwarding data to the destination device. Switches use layer 2 MAC addresses to forward data frames at layer 2 of the OSI model. Many enterprise switches will also combine layer 3 functionality in the switch. Layer 3 switches allow for routing traffic between VLANs.
Switches are vulnerable to DOS attacks; the content-addressable memory (CAM) is typically overloaded/flooded with spoof MAC addresses. Switches can be used for MITM when using Internet Protocol version 4 (IPV4) Address Resolution Protocol (ARP) broadcasting. They can also suffer performance degradation due to unwanted looping traffic.
Mitigation would include the following:
- Protect the management interface (use strong passwords).
- Enable Spanning Tree Protocol (STP) (this will block redundant connections) to prevent looping traffic.
- Connect using SSH (all management traffic is encrypted).
- Provide an out-of-band (OOB) network (all management is performed on a separate management network).
- Configure 802.1x (require all network connections to be authenticated).
The following screenshot shows what a switch table looks like:
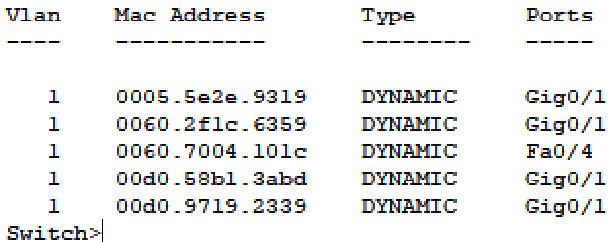
Figure 1.9 – Switch table
Switches provide essential services on enterprise networks and will be responsible for the bulk of all network traffic.
Firewalls
Firewalls are there to block unwanted traffic entering your networks; they can also block outbound traffic. They depend upon rules to block IP addresses, protocols, and ports. More sophisticated firewalls will have more granular rules and may slow down traffic.
Firewall types
Firewalls can be implemented in many different ways; enterprise deployment will have highly capable hardware solutions from vendors such as Cisco or Check Point. Software or host-based firewalls offer additional security with DiD. Data centers and microsegmentation will accelerate the use of virtual firewall deployment. Different types of firewalls are listed here:
- Hardware firewalls provide maximum performance. These are typically dedicated appliances with a central processing unit (CPU) and memory dedicated solely to this function.
- Software firewalls generally run on a host operating system, such as Microsoft Windows Defender Firewall or Linux iptables. They share computing resources with the operating system.
- Virtual firewalls are appliances running on a virtual host controlled by a hypervisor. The performance is dependent upon the compute resources allocated by the hypervisor.
Firewall capability
Firewalls have evolved over time, with additional capabilities and functionality.
First-generation firewalls use static packet filtering. They inspect packet headers and implement static rules based upon IP addresses and port addresses. Their big advantage is high performance. A router will typically perform as a static packet filter.
Second-generation firewalls also use stateful inspection, in addition to packet filtering. This can monitor Transmission Control Protocol (TCP) streams (whole stream, not just handshake) and dynamically open ports and track sessions for bi-directional protocols (such as File Transfer Protocol (FTP)).
Next-generation firewalls (NGFWs) have evolved from second-generation firewalls to meet the requirements of a multi-functional security appliance. An NGFW offers all the functionality of the earlier generation, but will typically offer additional functionality in the form of support for VPNs and anti-virus protection. NGFWs have DPI capability, meaning they can offer additional security in the form of DLP and IPS protection. This should not be confused with UTM, although they are similar. NGFWs are designed with performance in mind.
Routers
Routers operate at layer 3 of the OSI model and are interconnection devices (they connect networks together). Routing capability may also be provided by a switch that supports VLANs (it will be called a layer 3 switch).
Routing tables
Routers are only able to forward packets if they have a route for the traffic or a default gateway. Routing tables will comprise a NETWORK DESTINATION, NETMASK, GATEWAY, INTERFACE, and METRIC value.
Here is a simple routing table:

Figure 1.10 – Routing table
Static routing tables may be acceptable for small networks, but we will need to support automated dynamic routing for larger networks.
Dynamic routing
In larger, more complex networks, it is normal to use dynamic routing rather than configuring manual static routes. Within an autonomous network (the network managed by your organization), you will be using interior routing protocols. It would be time-consuming to configure routing tables statically and we would miss the resilience offered by dynamic routing protocols.
The purpose of dynamic routing protocols includes the following:
- Discovering available remote networks
- Maintaining up-to-date routing information
- Choosing the most efficient path to remote networks
- Allocating a new path if a route is unavailable
Routing Information Protocol (RIP) is the simplest and easiest routing protocol to configure. It is used for routing over smaller networks (allowing a maximum of 15 hops). It is not considered a secure routing protocol.
Enhanced Interior Gateway Routing Protocol (EIGRP) is used on Cisco networks and was developed to work around the drawbacks of using RIP. EIGRP benefits from fast convergence times whenever the network topology is changed.
CISCO devices share their capabilities using Cisco Discovery Protocol (CDP) with immediate neighbors. This can be disabled on a network.
You can prevent your router from receiving unwanted/poisoned route updates by configuring neighbor router authentication; this uses Message Digest 5 (MD5) authentication.
Open Shortest Path First (OSPF) is a good choice for larger networks because it has no restriction on hop counts. OSPF allows routers to communicate securely, and routing information is exchanged through link-state advertisements (LSA). RFC 2328 allows for the use of a keyed MD5 identifier to protect OSPF neighbor updates.
Exterior routing
To keep internet working routing tables up to date, edge routers will forward route changes via exterior routing protocols.
Border Gateway Protocol (BGP) is the routing protocol used between internet service providers (ISPs). BGP can also be used to send routing updates between an enterprise and its ISP. BGP can be secured so that only approved routers can exchange data with each other (this uses MD5 authentication).
Proxy
A proxy server acts as a gateway between users and the internet services they access online.
A proxy protects your users from directly connecting with unsafe sites. It can offer Uniform Resource Locator (URL) filtering and content filtering in addition to performance enhancements. A proxy can be a good choice when protecting our users from threats based upon outbound requests. Firewalls are not designed to deliver this more granular protection. A firewall could block an outbound connection to a port and IP address, but would not offer the same fine-tuning as a proxy server.
Network address translation gateway
Network address translation (NAT) is a networking technique commonly used to give an entire private network access to the internet without needing to assign each host a public IPv4 address. The hosts can create connections to the internet and receive responses but will not receive inbound connections initiated from the internet (as they are, in effect, hidden). The following diagram shows a NAT router forwarding traffic to the internet from an internal host:
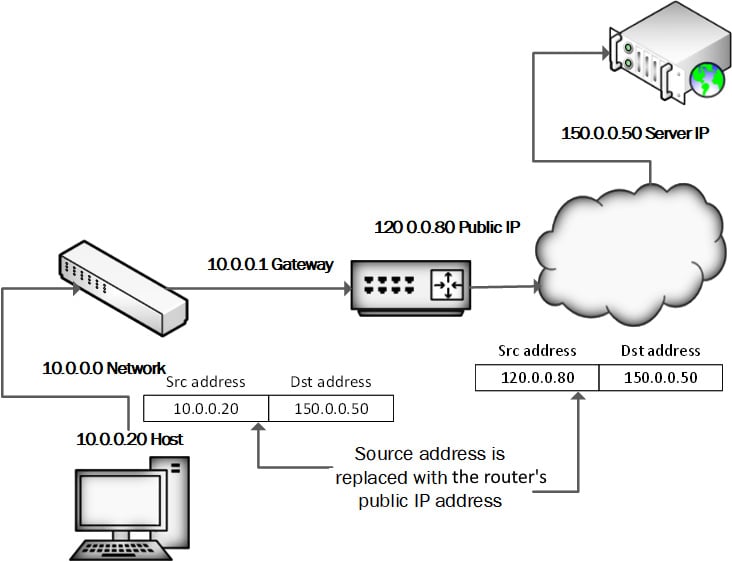
Figure 1.11 – NAT routing
When a host on the internal (private) network sends a request to an external host, the NAT device's public IP address is used as the new source IP address for the outbound traffic. The traffic sent back in reply is returned to the internal host. Most NAT solutions use port address translation (PAT) to keep track of all the private hosts that have sessions. We can see NAT configuration in the following screenshot:

Figure 1.12 – Microsoft Routing and Remote Access Service (RRAS) with connected clients
NAT is an important service used in both enterprise and small business deployments.
Load balancer
A load balancer will be useful to enterprises that host server farms and would be a key requirement for high availability (HA) e-commerce sites. When hosting a Citrix server farm supporting remote applications, it is important that the loading on each member is constantly evaluated to ensure new requests are forwarded to a server with the least load.
Hardware security module
A hardware security module (HSM) is a special trusted network computer performing a variety of cryptographic operations: key management, key exchange, encryption, and so on. This device can be a rack-mounted appliance secured in your data center or could be a built-in module for high-end server hardware.
A trusted platform module (TPM) is typically built into system boards of laptop and desktop computer systems, allowing for the storage of sensitive protected data, including keys and attestation measurements. This is a good example of an HSM incorporated into the system board.
MicroSD HSM is built into a MicroSD form factor. It is useful when you need to extend the functionality of a mobile device and could be used on a cellular phone for secure communications. The HSM would have its own crypto-processing capability, meaning no changes are required on the mobile device. The following screenshot shows a small form-factor HSM:

Figure 1.13 – MicroSD HSM
Many of the security applications mentioned up to this point secure the entire network from threats. In the following section, we will examine more targeted/granular approaches to protect particular services or data types.

























































