Challenges facing incident response
IR is a fairly challenging process, and IR teams meet a fair share of challenges when carrying it out. Every organization is susceptible to attacks, yet it is upon IR teams to ensure the protection of the organization, its healthy reputation, and customer trust, and moreover ensure that a similar threat will not reoccur in the future.
When a security incident occurs, confusion might hit organizations, especially if they have never handled similar security events before. An informed IR plan guides organizations, regardless of prior experiences, on how to handle each aspect of an incident. IR also mitigates the effects of a security event, to ensure minimal damage and fast recovery of key business processes. Therefore, depending on the stage of an attack or intrusion, the IR plan will detail the steps that must be taken to ensure the best outcomes for the organization. Without this guiding tool, the organization would find it hard to systematically contain any security event.
However, there are still many issues that arise in the wake of an attack that an IR team will need to effectively counter. The following section will detail some of the main challenges facing IR teams. We'll start by considering the importance of protecting the company brand.
Protecting the company brand
One major challenge facing IR teams is protecting their organization's brand, as IT security is closely tied to the reputation and valuation of an organization. As observed in recent breaches, poorly handled security incidents hurt the brands of the affected companies. For instance, Yahoo's valuation dropped by 350 million US dollars after a hack in 2017 that was reported to have affected one billion users. Similarly, a report by Kacy Zurkus indicated that the common aftermath of security breaches in organizations is a decrease in stock price.
Zurkus' article can be accessed here: https://www.infosecurity-magazine.com/news/companies-stock-value-dropped-1/.
Zurkus estimated the average drop of stock value to be 7.5%. However, security incidents, if correctly handled, might not have such a dramatic effect on the brand of the company. Due to effective incident management, Sergei Klebnikov reports that big-name companies that have been victims of security breaches mostly recover and outperform the market in as little as six months after the breach.
Klebnikov's article can be accessed here: https://www.forbes.com/sites/sergeiklebnikov/2019/11/06/companies-with-security-fails-dont-see-their-stocks-drop-as-much-according-to-report/#29da9aed62e0.
Examples of post-incident activities in such companies might include more optimized customer relationship management, to ensure that the existing clientele is retained and new customers are strategically acquired. Thus, IR faces a crucial challenge in providing ways that the organization can prevent negative publicity as a result of cyber-attacks, and thereby maintain or increase its market share.
As you can see in Figure 2.4, many well-known corporations have experienced cyber incidents or been hacked:

Figure 2.4: Organizations that have fallen victim to cybercrime
As goes the popular phrase:
"There are two types of organizations: the ones that know they've been hacked and the ones that don't."
Preventing future breaches
As discussed in Chapter 1, Getting Started with Incident Response, the last phase of an incident management plan is reporting, and avoidance of future security incidents. Therefore, a major challenge facing IR teams is to identify the exploited vulnerability and implement permanent fixes to prevent the incident from reoccurring, leading to a better-secured organization. Some of these fixes include setting up schedules for patching, security evaluations, and backups to ensure that the organization will be best placed to deal with any future security incident. Therefore, IR acts as a preventative measure for future potential attacks.
Preparing for attacks
With the increased number of attacks, organizations are challenged to adopt and increase their cyber resilience, to survive security breaches. One of the ways to ensure resilience is by having IR teams and plans that are ready at all times. IR teams and IR plans are two tools that are part of the larger defense mechanism that an organization develops to ensure the security or recovery of its core assets during and after a security incident. IR entails building a competent team and structuring highly effective response plans that can be activated when required. Therefore, this challenge involves planning how to ensure the defense or survival of the organization before the actual attacks begin. We'll continue to consider this challenge with a discussion on the concept of cyber resilience in the next section.
Developing cyber resilience
Cyber resilience is a new approach to security that recognizes the threat of persistent, changing attacks. Having a resilient cybersecurity strategy that enables organizations to respond to inevitable breaches is key, rather than hoping that the data will never be compromised. As such, cyber resilience is a crucial counterpart to cybersecurity. As mentioned earlier, there are no shortcuts in cybersecurity, so it's important to adopt a long-term strategy, as illustrated in the following figure:
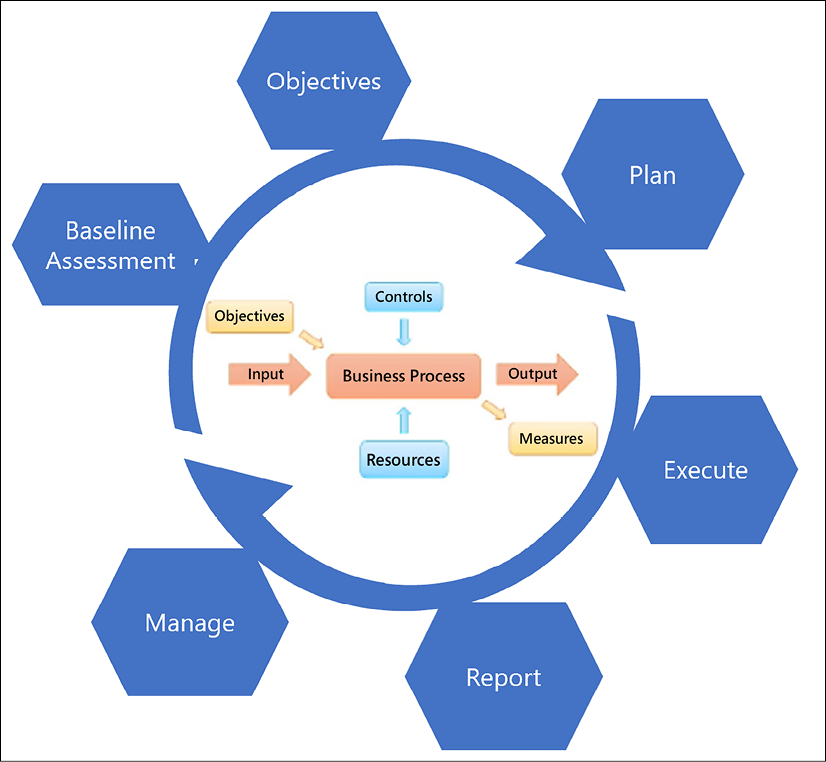
Figure 2.5: Cyber resilience strategy steps
The steps on how you can develop a long-term cyber resilience strategy are as follows:
- Baseline Assessment: This is the step in which you will need to align your organization's business requirements to your operational capabilities, and determine how you can build a successful strategy.
- Objectives: In this step, you will need to identify your resources and controls to ensure that your operational objectives are fully aligned with the strategy.
- Plan: Agree on an initial plan of action, which includes working with third-party partners.
- Execute: This step is when the plan will be carried out.
- Report: Have an outcome of the strategy in the short term (30 days), mid-term (60 days), and the long term (180 days). You can change the number of outcome days based on your needs. This is based on the Objectives and Inputs, which will need to be fed into the Business Process (see the flowchart at the center of Figure 2.5), based on your organization's Controls and Resources. These steps will help us to generate the Output (report) and Measures to take.
- Manage: Your IR plan needs to be continually updated and managed accordingly.
Now, let's consider another challenge that faces IR teams: security safeguard assessment.
Assessing security safeguards
IR is modeled around the organization's existing defense mechanisms. Thus, during the development of an IR plan, a challenge the organization faces is to assess all other defenses to work out a way they will work with the IR team. Commonly, network security tools, enterprise and host-based antivirus systems, endpoint detection and response systems, intrusion detection systems, cloud connections, and user awareness training are considered and evaluated when setting up an IR plan, as illustrated in Figure 2.6:
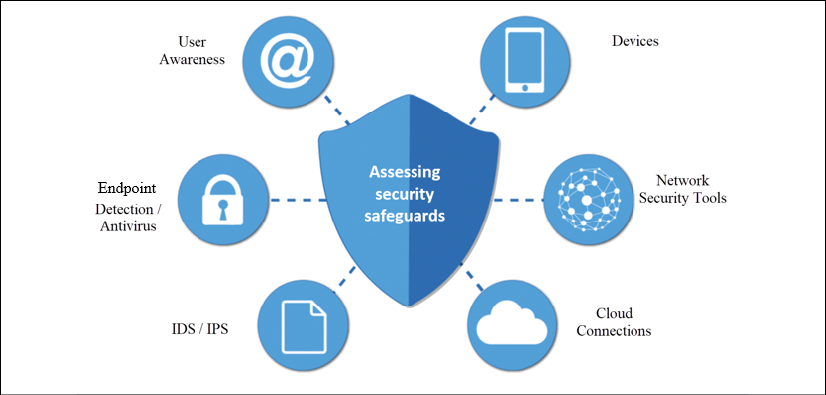
Figure 2.6: Assessing your security safeguards
The assessment of these tools provides room for the organization to find weaknesses in the safeguards and make changes to ensure better security.
Aiding investigations and legal prosecutions
In the IR process, the third phase is the investigation stage, where the IR team collects and examines evidence relating to the security incident. The evidence is retrieved from an assortment of sources such as logs, users, and security tools and may help identify the attacker or reveal the trails to other complacent parties. Eventually, the evidence can be used in the prosecution of suspects in court. Therefore, from a legal perspective, IR is important as it may help the organization win legal battles against suspected attackers, malicious employees, or unscrupulous third parties.
Figure 2.7: For collection evidence, tools like IREC can be used
Figure 2.7 illustrates how the IREC tool from Binalyze can help us to collect evidence, which we will demonstrate later, in Chapter 14, Incident Case Studies.
Bringing the organization together during crises
In most organizations, employees are grouped into functional units, hence they only concentrate on tasks pertinent to their departments. IR teams are composed of personnel from different departments who work toward preventing extensive damage and ensuring the recovery of the organization during security incidents. During security events such as attacks, each team member brings competencies from their respective departments. For instance, communication personnel will disseminate information as appropriate to all stakeholders during an attack, while an IT support specialist will be involved in stopping the execution of the attack. The collaboration of many departments in the IR process improves cohesion and cooperation in the organization even after the security incident has been dealt with.
Ensuring the integration of security initiatives
Organizations might have several security initiatives that work independently. For instance, many organizations have IT security policies, employee training programs, security awareness programs, IT auditing, change management plans, and penetration testing as part of their security framework. However, most of these initiatives are not integrated.
For instance, penetration testing exercises might not be connected to employee training programs. IR has a unifying effect on the existing security measures to bolster the defense capability of the organization. Therefore, during IR planning, all these tools will be identified and refined to work together to secure the organization. For example, during the planning process, related initiatives such as employee training and security awareness programs can be combined. Similarly, IT auditing and penetration testing could be made to complement each other in a situation where penetration testers identify weaknesses first, and IT auditors focus more on the problematic areas when examining the organization's IT assets.
Improving the overall security stature of the organization
Conventionally, organizations relied on cybersecurity tools to ensure the security of their organizations. Hence, only the IT department was tasked with cybersecurity-related functions. However, as the frequency, complexity, and intensity of attacks have grown, organizations have had to adopt more effective security measures to prevent, combat, and manage attacks. IR is one of the relatively new ways to improve the security stature of the organization. When all else fails and an attack permeates to the organization, the IR team can be tasked with eliminating the source and recovering the organization. Thus, security is no longer hedged just on security software but also on a highly effective team that will resolve security threats when they occur.
The following are six best practices you can use to improve your organization's security posture:
- Conduct a cybersecurity risk assessment
- Prioritize risk
- Track security metrics
- Implement automated cybersecurity solutions
- Educate your employees
- Create an IR plan
These categories will be explored throughout different chapters in this book.
The headings in this section have covered some of the main challenges faced by IR teams when carrying out IR. Mainly, these teams have to look at how they can secure the company's brand, prevent future attacks, improve security stature, integrate all security initiatives, assist with evidence collection to aid in investigations, and still be a strong unit that brings the organization together during crises.


























































