Setting up your environment
Depending on which hosting option you selected, your setup can be as easy as simply logging in with a newly provided user account to the cloud or consist of a lengthy configuration and set up with the on-premise deployment. The following are the requirements needed to get your environment set up based on your choice of deployment:
Shared SaaS
With the SaaS environment, you will have two options for deployment:
- Pure Cloud
- Integrated Cloud
The Pure Cloud option will have no integration with any of your enterprise systems. All accounts will be managed locally and there will be limitations on your deployment. This option might serve a purpose for a smaller organization that doesn't have enterprise systems or is just looking for a simple deployment of AirWatch.
Tip
If you move forward with this option, there could potentially be a lot of management needed with local accounts that need to be created and deleted.
The Integrated Cloud option or better known across the industry as Hybrid Deployment provides the same SaaS environment for management with the addition of integrations with your enterprise systems using AirWatch Cloud Connector (ACC), Mobile Access Gateway (MAG), and Secure Email Gateway (SEG). These integrations do require on-premise deployment of servers, which will be covered in Chapter 3, Enterprise Integration, and Chapter 7, Mobile Email Management.
With both of these options, getting started is easy. You will be provided with the URL to your environment and login details to gain access. Your URL will look something like https://cnxxx.awmdm.com, where xxx will be replaced with a number. Once you have this information and your login details, you are ready to start.
Tip
You can set up your own custom URL that is redirected to your SaaS environment.
Dedicated SaaS
The dedicated SaaS environment follows the same options as mentioned previously with the exception of the differences listed in the table present in the Hosting options section of this chapter. There are a few reasons to select this option but the primary reason is to gain more control over when updates and Feature Packs can be deployed.
To get started with your dedicated SaaS, you will be provided with the URL to your environment and login details to gain access. Your URL will look something like https://cnxxx.awmdm.com, where xxx will be replaced with a number. Once you have this information and your login details, you are ready to start.
Tip
You can set up your own custom URL using a CNAME DNS record. The recommended configuration is to set up your CNAME record to point to the AirWatch CNAME record, which will direct to the AirWatch Host A record. The reason for this is to allow AirWatch to gain control over where the records point in the event of a failover. If you point your CNAME record directly to the AirWatch Host A record, you will delay the time of a failover, as you will be required to update your DNS records.
On-premise appliance
As an alternative to setting up and configuring your on-premise deployment, AirWatch provides us with the opportunity to use an appliance. The appliance is preconfigured by AirWatch, shipped to the customer ready to simply deploy in the network and turn on.
The following is the sizing chart provided by AirWatch:
|
Max number of devices |
100 |
500 |
1,000 |
2,500 |
5,000 |
|---|---|---|---|---|---|
|
Number of appliances |
1 |
1 |
1 |
1 |
1 |
|
CPU cores |
3 |
3 |
4 |
4 |
4 |
|
RAM (GB) |
4 |
4 |
4 |
8 |
8 |
|
Hard disk (GB) |
21 |
35 |
50 |
95 |
185 |
Tip
The following are important to know as part of the appliance deployment:
- It is not recommended to enroll more devices than stated per configuration
- Windows server and SQL licenses are included with the appliance
- You will need multiple appliances and your own load balanced solution to provided HA/Failover
On-premise deployment
The last option is the on-premise deployment, that is, giving the customer full control and flexibility over the deployment. This option will require a lot of planning and involvement from multiple teams in order to make it successful.
Since this book is focused more around learning AirWatch, I will not go into deep detail on all the different architecture and options with setting up AirWatch, as this information can easily present itself in its own book. Instead, I will give a high-level overview of the options and requirements to get AirWatch set up.
Before you get started with your on-premise deployment, you will need to fully review the architecture and pre-installation documents provided by AirWatch. You will need to size your environment correctly based on the number of devices you plan to enroll plus future growth.
For the setup and configuration, you will need to involve multiple technical teams with the deployment:
- The Application/Mobility team (Application owner of AirWatch)
- The Database team (SQL database installation and management)
- The Systems management team (provide servers and monitoring)
- The Storage team (provide all storage requirements)
- The Network team (provide Firewall changes, HLB, and other network changes)
- The Security team (validated configurations meet security needs)
Components
For your on-premise deployment, there are three required components:
- AirWatch Admin Console: This is the web console used by administrators to set up, configure, and manage devices
- Device services: This component allows AirWatch to communicate with the devices
- SQL database: All AirWatch information is contained within the SQL database
In addition to the required components, there are several optional components:
- AirWatch SEG: Allows greater integration, control, and security with enterprise e-mail systems. This will be covered in detail in Chapter 7, Mobile Email Management.
- AirWatch Cloud Messaging (AWCM): AWCM allows AirWatch to directly send commands to Android, Symbian, and Windows mobile devices and push products to PCs and Mac OS X. This allows the elimination of Google Cloud Messaging (GCM) for Android devices and reduces security concerns by eliminating communication over public networks.
- AirWatch Cloud Connector (ACC): ACC provides enterprise integrations with multiple different components within the network. This will be covered in more detail in Chapter 3, Enterprise Integration.
- AirWatch Mobile Access Gateway (MAG): MAG allows secure integration with enterprise applications and sites and content repositories. This will be covered in more detail in Chapter 3, Enterprise Integration; Chapter 8, Mobile Content Management; and Chapter 9, Mobile Application and Mobile Browser Management.
- AirWatch App Wrapping: This allows an organization to add additional security and data loss prevention by wrapping the applications before deployment. This will be covered in more detail in Chapter 9, Mobile Application and Mobile Browser Management.
Configurations
There are multiple configurations available with all the different components provided by AirWatch. In summary, the following configurations are provided as examples from AirWatch:
- Basic/Single Application Server Deployment
- This is recommended for managing less than 1,000 devices
- This includes all the components on a single server
- This allows simplified installation, configuration, and integration
- Hybrid Server Deployment
- This is recommended for managing between 1,000 and 5,000 devices but can be used for less if desired
- This solution combines only the Admin console, AWCM and Device Services components onto one server
- Dedicated server for SQL database
- Dedicated server for SEG and other optional components
Tip
Plan to deploy the application server within a DMZ if possible for additional security.
- Multiple Server Deployment
- This is recommended for managing more than 5,000 devices but can be used for less if desired
- This solution allows the deployment of components on their own dedicated servers
- Provides greater security by deploying specific components within the DMZ and others on internal network
Tip
Because of the complexity and requirements for this deployment, it is recommended to work with AirWatch on the architecture and configuration.
Requirements
The following tables will give you an idea of the hardware requirements needed for your on-premise deployment:
Application server
|
Max number of devices |
100 |
500 |
1,000 |
2,500 |
5,000 |
10,000 |
25,000 |
|---|---|---|---|---|---|---|---|
|
Admin Console |
1 standard app server for all roles Virtual Machine / 2 CPUs / 4 GB RAM |
1 app server per 50 concurrent admins | |||||
|
Device Services |
1 app server |
2 app servers | |||||
|
Device Services with AWCM |
1 app server |
2 app servers | |||||
Database server
|
Max number of devices |
100 |
500 |
1,000 |
2,500 |
5,000 |
10,000 |
25,000 |
|---|---|---|---|---|---|---|---|
|
CPU cores |
1 |
1 |
2 |
2 |
2 |
4 |
8 |
|
RAM (GB) |
4 |
4 |
4 |
8 |
8 |
16 |
32 |
|
DB size(GB) |
10 |
20 |
25 |
50 |
100 |
175 |
250 |
|
Trans log size(GB) (Log backups every 15 minutes) |
3 |
5 |
10 |
20 |
40 |
50 |
100 |
|
Temp DB (GB) |
3 |
5 |
10 |
20 |
40 |
50 |
100 |
|
Avg IOPS (DB and temp DB) |
30 |
30 |
30 |
75 |
150 |
300 |
750 |
|
Peak IOPS (DB and temp DB) |
40 |
50 |
60 |
150 |
300 |
600 |
1500 |
Note
There are also minimum requirements and deployment architecture for 50,000 or more devices that can be provided by AirWatch.
Console and device services connectivity prerequisites
Before you can get started with the installation of the console and the device services connectivity server(s), you need to meet all the prerequisites. The following is a breakdown of what is needed before you can start the installation:
The hardware requirements are as follows:
- A VM or physical server
The general requirements are as follows:
- Remote access to Windows servers
- Notepad++ (recommended)
- Firefox or Chrome (recommended)
- Service accounts for authentication to enterprise systems
- Test devices (iOS, Android, Windows Phone 8)
- Corporate Apple ID—if your deployment includes iOS devices, you will need to generate Apple APNs certificate, which is available at https://appleid.apple.com
- Corporate Google ID—this is required to search Play Store and push applications to the devices
The software requirements are as follows:
- Externally and internally registered DNS (public IP addresses)
- SSL Certificate from trusted third party with Subject or Subject Alternative Name (SAN) of Domain Name System (DNS)
- Windows Server 2008 R2 or 2012 or 2012 R2
- Installation of IIS Role with the following services from Server Manager:
- Common HTTP features: Static Content, Default Document, Directory Browsing, HTTP Errors, HTTP Redirection
- Application development: ASP.NET, .NET Extensibility, ASP, ISAPI Extensions, ISAPI Filters, Server Side Includes (SSI)
- Health and diagnostics: HTTP Logging, Logging Tools, Request Monitor, Tracing Security: Request Filtering, IP, and Domain Restrictions
- Performance: Static content compression, dynamic content compression
- Management tools: IIS Management Console, IIS 6 Metabase Compatibility
Note
Note that Ensure WebDAV is not installed.
- Installation of the following features from Server Manager:
- .NET Framework 3.5.1 features: Entire module(.NET Framework 3.5.1, WCF activation)
- Message queuing: Message Queuing server
- Telnet client
- Installation of 64-bit Java Runtime Version 7 or higher
- IIS 443 binding with the same SSL certificate (device services only)
- Installation of .NET Framework 4.0
- Microsoft URL Rewrite Module 2.0
Note
Additional proxy software might be required for communication to Apple devices, App Store, and Google Play Store.
The database and reporting services requirements:
- SQL Server 2008 R2 or 2012 running in the 2008 compatibility mode
- Creation of AirWatch database
- SQL collation is
SQL_Latin1_General_CP1_Cl_AS - SQL account permissions:
db_owneron the AirWatch databasedb_datareader, public, and SQLAgentUserRole on MSDB
- Ensure Full-Text Search is installed on SQL database
- Reporting services installed and configured in SQL Management Studio
- Reporting services configured with user, password, and database
- Validate SQL account permissions:
db_owneron theReportServer<Instance>databasedb_owneron theReportServerTempDB<Instance>database
- Validate that the Web services URL is reachable
- Validate that the Report Manager URL is reachable
- Validate that the Web services URL is reachable from Console server
The network requirements are as follows:
There are multiple ports that need to be opened on your corporate firewall in order to allow AirWatch to work correctly. The following will need access to internal and/or external Internet resources:
- Admin console server
- Device services server
- SQL server reporting
- Devices (Internet/Wi-Fi)
- Apache Tomcat server
Note
You will need to work closely with your network team to ensure that all the ports on the firewall are opened correctly. There is over four pages of protocol/port configurations to multiple external URLs needed. The required protocol/port configurations can be found in AirWatch On-premise technical architecture guide.
It is highly recommended to implement redundancy with a load balancer. These configurations should be implemented: Round Robin, Session Persistence for Device Services, and Admin Console and redirect all HTTP requests to HTTPS.
The preinstallation check
After implementing all the requirements, you can use AirWatch's preinstallation tool to validate that your on-premise environment is ready to install AirWatch Application server. Once the tool is open, select Application Server and then follow the instructions to validate. You will be presented with the results and what needs to be resolved if there is anything.
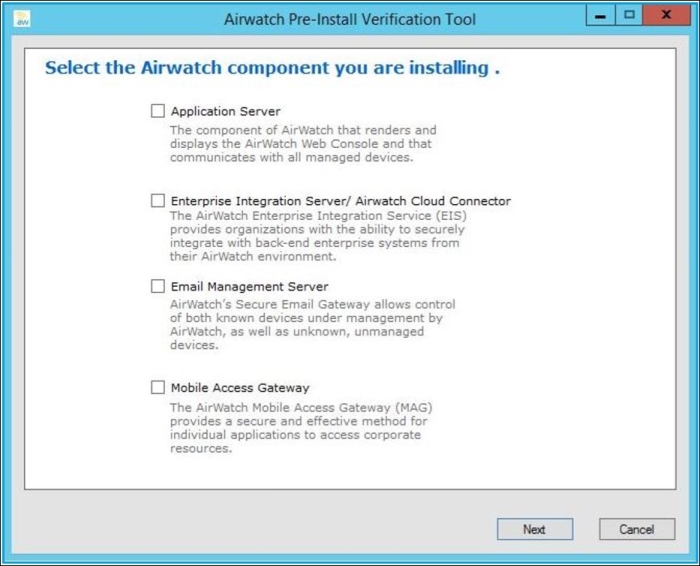
Once you have everything set up correctly, you will be ready to install your environment. AirWatch will provide you with the necessary installation files and services to get your environment up and running on premise.
Deploying AirWatch On-premise will require a lot of preparation and planning, which will require a dedicated senior-level architect/engineer to fully understand the complexities and requirements needed to set up the environment. Unless your organization has a no-cloud policy, it is highly recommended to move forward with a SaaS deployment to allow your teams to focus more on the services being delivered and more importantly, a successful mobile strategy.























































