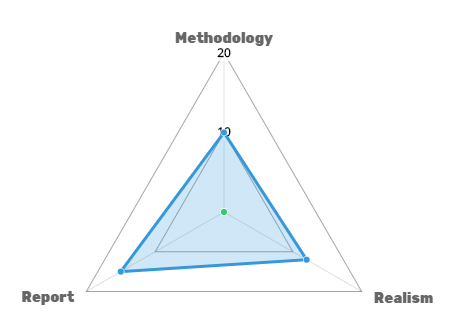
Penetration testing like any systemic methodology needs to be evaluated to provide useful insights about the reliability of the used methodology. A well-designed pentesting approach and a good evaluation strategy should be based on quantified approved criteria, to quickly determine the depth and the quality of testing. Industry leaders are aware of all well-known penetration testing methodologies, but due to some understanding difficulties, many of these companies are using their own methodologies. An effective penetration testing program assures that the objectives of your penetration testing program were met without creating misunderstandings, misconceptions, or false expectations. A maturity model is needed to assure that the pentesting methodology meets the organization needs; you can build the most suitable maturity model for your organization needs. You can get inspired by a penetration testing model made by voodoo security. It is built to give an idea about such models.
The penetration testing maturity model is based on three main criteria. Each criteria has five questions to answer by yes or no. If yes, the overall score will be added by one point, else, it will add nothing. Based on your responses to all the questions, the overall score will define the evaluation of your penetration test.