To use Burp as a tool for application penetration testing, it must be set as a Man in the Middle (MITM) proxy. An MITM proxy sits in between a client and a server, and allows the user to tamper or drop messages passing through. In its simplest form, Burp Suite is an MITM proxy for HTTP(S) traffic.
By default, Burp will listen on port 8080 on the localhost IP of 127.0.0.1. This can easily be changed, however, to an arbitrary free port on any IP address available on the system. To do this, follow these steps:
- Navigate to the Proxy | Options tab.
- Under Proxy Listeners, confirm that the Running checkbox is ticked in front of the proxy entry.
- If the checkbox refuses to check, even after you have clicked it, it very likely means that the port selected (default 8080) is being used by another process on the system. You can simply choose another port to start listening for connections:
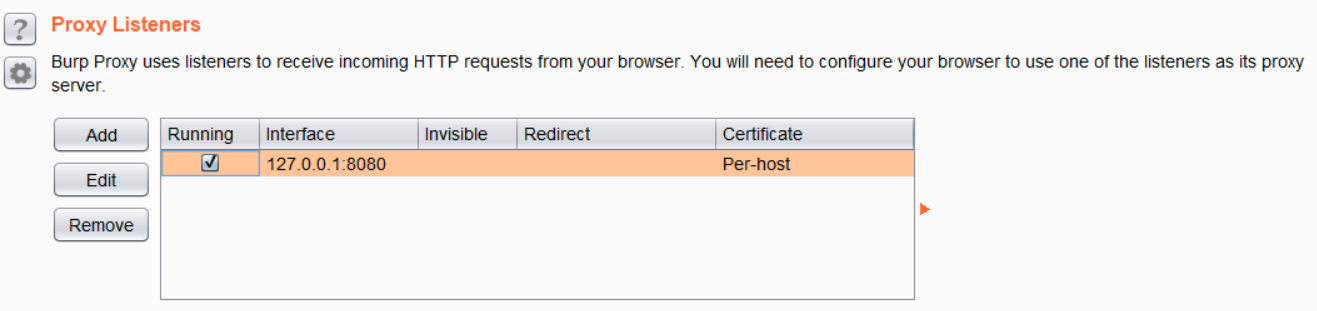
If there is no Proxy Listener listed at all (it's rare, but this does happen), follow these steps to set up a new proxy listener:
- Click on Add.
- In the Add a new proxy listener window that opens, under the Binding tab enter a port to bind to, which would typically be 8080.
- Set the Bind to address to Loopback only, and click OK to create the listener.
If you plan on using Burp over the network, then you can select an interface from the drop-down list in front of the Specific address option. Be careful when using this option as this allows any user on the network to proxy traffic through your system, and allows access to the contents of the Proxy History, which may contain sensitive information, such as session cookies and login credentials. Enable this only if you trust the network you are on:
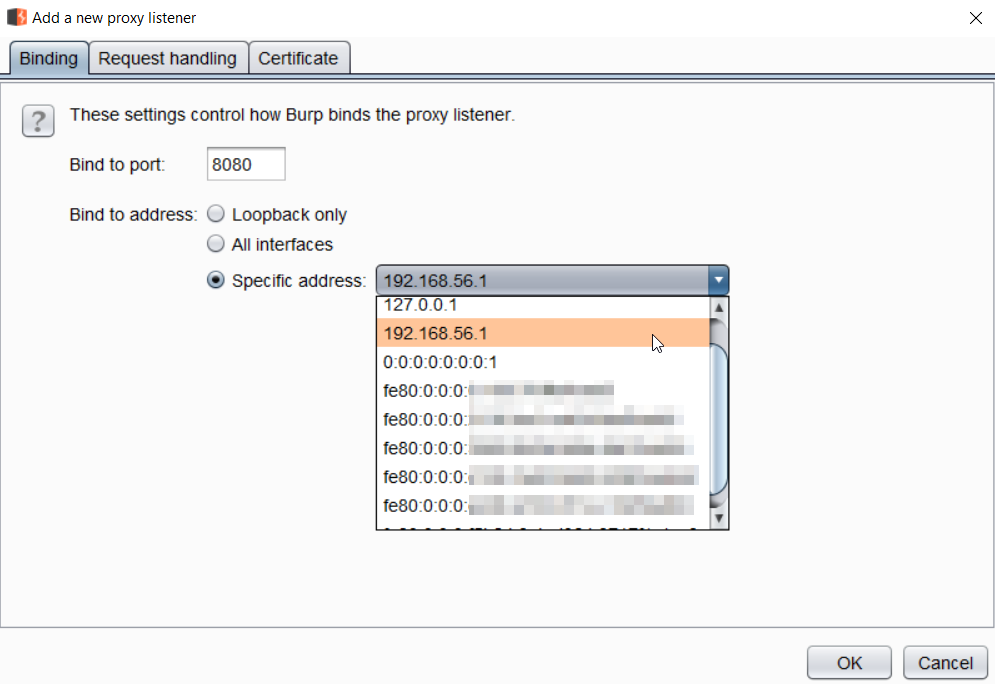
If the proxy listener checkbox does not toggle to a check, it very likely means that another process on the system is listening on that port. On Windows, you can use the netstat -antob command to identify ports and the processes that are using the open port. On Linux and macOS, use the netstat -lntp command. Both need to be run in an elevated environment on their respective operating systems.
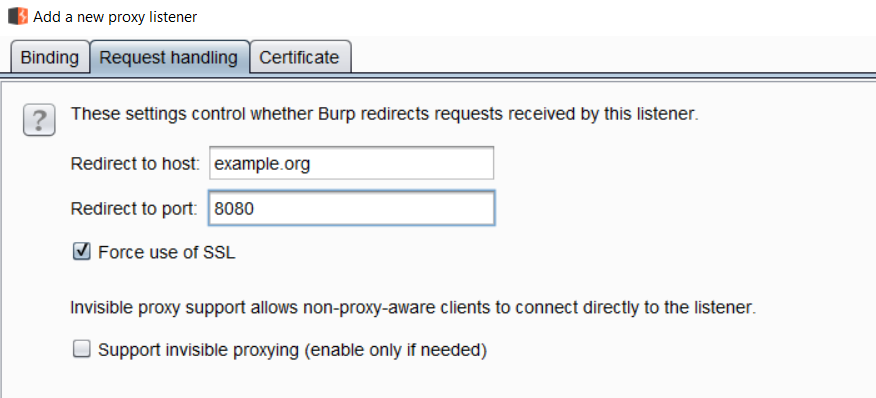
A proxy listener can be configured for various Request handling use cases. The following options are available here:
- Redirect to host: When configured, Burp will forward every request to the specified host, regardless of the original target requested by the user agent.
- Redirect to port: When configured, Burp will forward every request to the specified port, regardless of the original port requested by the user agent.
- Force use of SSL: When configured, Burp will force HTTPS on all outgoing traffic, even when the request that originated from the user-agent was HTTP:
The Certificate tab allows you to configure various SSL-related options, and to fix errors that may arise during a penetration test. The following options are available on this page:
- Use a self-signed certificate: A self-signed certificate is generated and given to the browser. This will always cause an SSL alert on modern browsers.
- Generate CA-signed per-host certificates: This is the default option selected when a new proxy listener is created. When Burp is first run, a self-signed Certificate Authority (CA) certificate is created. This certificate can be installed as a trusted root in your browser by clicking on the Import / export CA certificate button, or from http://127.0.0.1:8080/cert (when the proxy listener is on port 8080), so that the per host certificates can be accepted without any alerts.
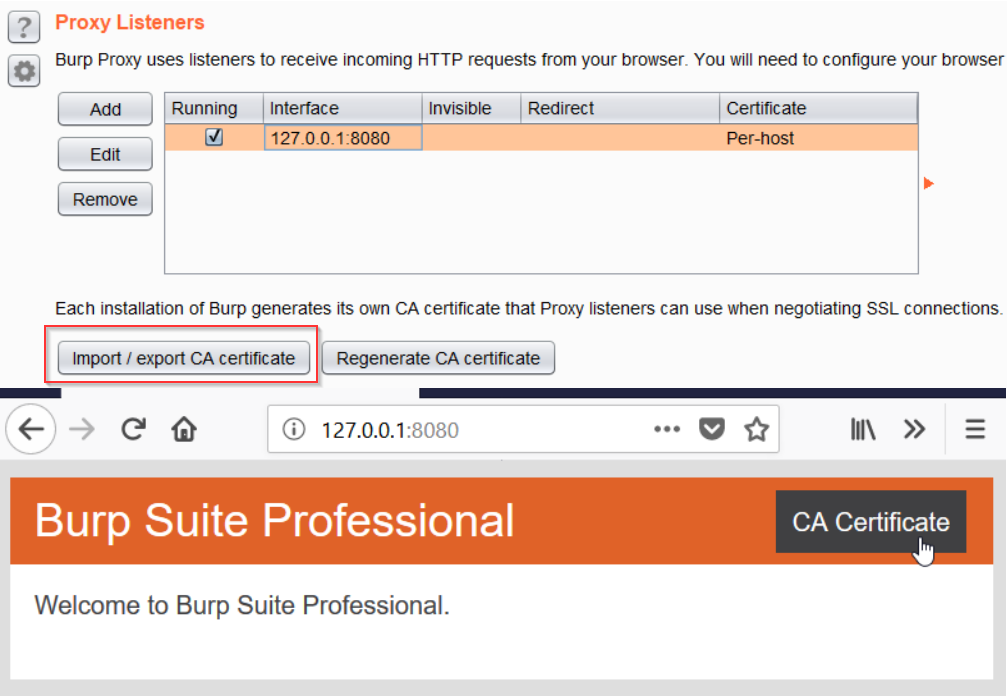
- Use a custom certificate: This option allows Burp to use a custom PKCS#12 format certificate.
Throughout the book, unless otherwise specified, we will be using the default option for SSL certificates.
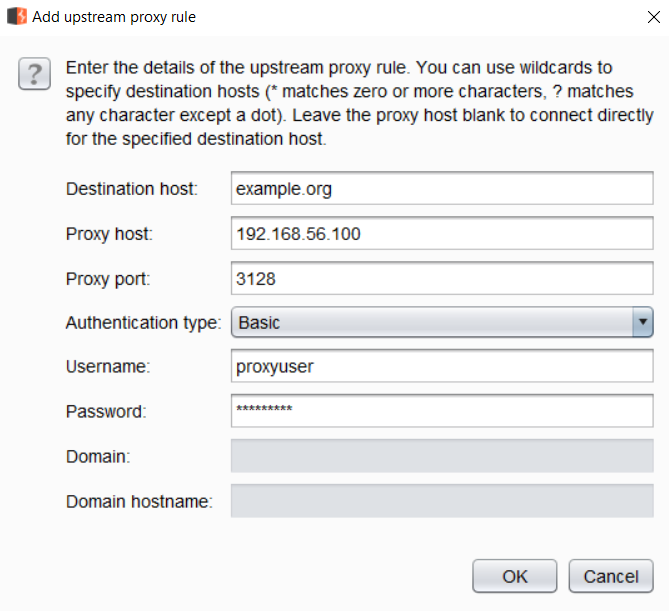
Another very important feature that we must be aware of at this point is Burp's capability to chain multiple proxies. As with most settings in Burp, setting upstream proxy servers or SOCKS proxies can be configured in great detail.
To set an upstream proxy server, or to basically to configure Burp to forward the request to the destination web server, or to additional proxies, click on the User Options tab in the main window and scroll down to Upstream Proxy Servers. To configure an upstream proxy for all destinations, use a wildcard (*) operator.
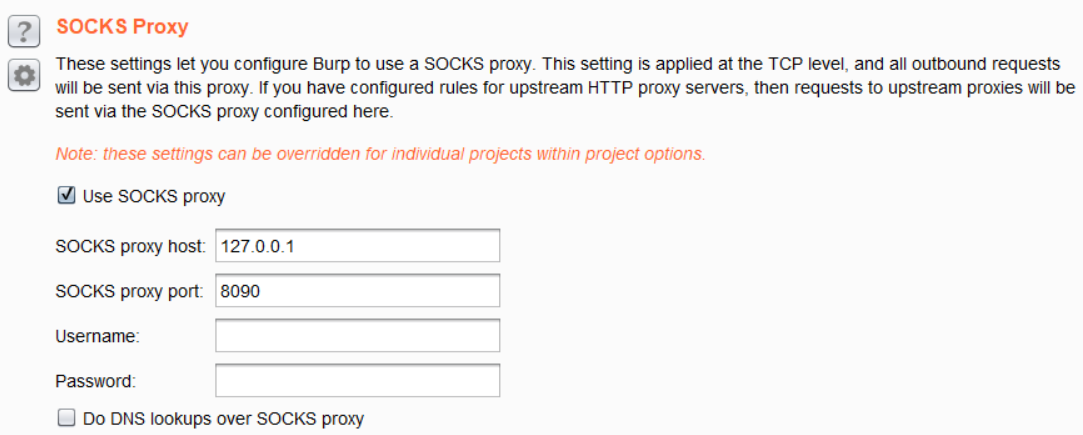
Sometimes, customers require an IP address from which all attack traffic would originate to the end customer. In this case, simply running a Linux machine with a static IP on the internet and SSH with port forwarding enabled allows Burp to proxy its traffic through the SOCKS Proxy that this arrangement creates.
 Germany
Germany
 Slovakia
Slovakia
 Canada
Canada
 Brazil
Brazil
 Singapore
Singapore
 Hungary
Hungary
 Philippines
Philippines
 Mexico
Mexico
 Thailand
Thailand
 Ukraine
Ukraine
 Luxembourg
Luxembourg
 Estonia
Estonia
 Lithuania
Lithuania
 Norway
Norway
 Chile
Chile
 United States
United States
 Great Britain
Great Britain
 India
India
 Spain
Spain
 South Korea
South Korea
 Ecuador
Ecuador
 Colombia
Colombia
 Taiwan
Taiwan
 Switzerland
Switzerland
 Indonesia
Indonesia
 Cyprus
Cyprus
 Denmark
Denmark
 Finland
Finland
 Poland
Poland
 Malta
Malta
 Czechia
Czechia
 New Zealand
New Zealand
 Austria
Austria
 Turkey
Turkey
 France
France
 Sweden
Sweden
 Italy
Italy
 Egypt
Egypt
 Belgium
Belgium
 Portugal
Portugal
 Slovenia
Slovenia
 Ireland
Ireland
 Romania
Romania
 Greece
Greece
 Argentina
Argentina
 Malaysia
Malaysia
 South Africa
South Africa
 Netherlands
Netherlands
 Bulgaria
Bulgaria
 Latvia
Latvia
 Australia
Australia
 Japan
Japan
 Russia
Russia


















