AWS is responsible for securing the global infrastructure that includes regions, availability zones and edge locations running on the AWS cloud. These availability zones host multiple data centers that house hardware, software, networking, and other resources that run AWS services. Securing this infrastructure is AWS’s number one priority and AWS is regularly audited by reputed agencies all over the world to meet necessary security and compliance standard requirements. These audit reports are available to customers from AWS as customers can't visit AWS data centers in person.
The following figure depicts the broader areas of security that fall under AWS' responsibility:
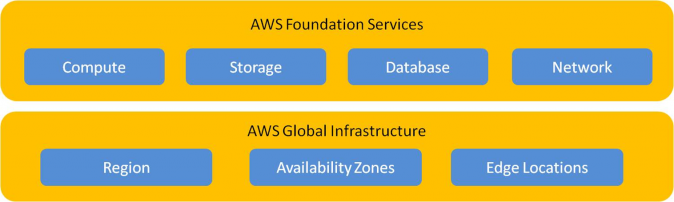
Customer data and workloads are stored in AWS data centers, these data centers are spread across geographical regions all over world. These data centers are owned, operated and controlled by AWS. This control includes physical access and entry to these data centers and all networking components and hardware, and all other additional data centers that are part of AWS global infrastructure.
Let us take a closer look at other responsibilities that AWS owns for securing its global infrastructure:






























































