What is a CSP policy?
Some policies can only be configured at the device level, whereas other policies can be configured at the user level. This means that device-level policies will have an effect independent of the user logging in to the device, whereas user-level policies will only have an effect depending on the user logging in to the device. As an example, different users can have different homepages in Microsoft Edge, so it is appropriate to assign a policy with that setting to a user group, whereas security settings that need to be applied at the device level are appropriate to assign to device groups.
User scope is where the policy only applies to the user who logs in to the device, and the policy can vary depending on who is logging in to the device. The following is an example of what the CSP tree looks like when configuring a user policy:
./User/Vendor/MSFT/Policy/Config/AreaName/PolicyNameis used to configure the policy../User/Vendor/MSFT/Policy/Result/AreaName/PolicyNameis used to get the result.
Device scope is where the policy only applies to the device itself, regardless of the user who logs in to the device. The following is an example of what the CSP tree looks like when configuring a device policy:
./Device/Vendor/MSFT/Policy/Config/AreaName/PolicyNameis used to configure the policy../Device/Vendor/MSFT/Policy/Result/AreaName/PolicyNameis used to get the result.
The biggest difference between a GPO and a CSP policy is that a CSP policy has a result channel as well, so every setting that is configured on the device will report back to the MDM system – in this case, Microsoft Intune.
If we take a closer look at the policy structure, it looks like the Windows registry is arranged in a tree structure:
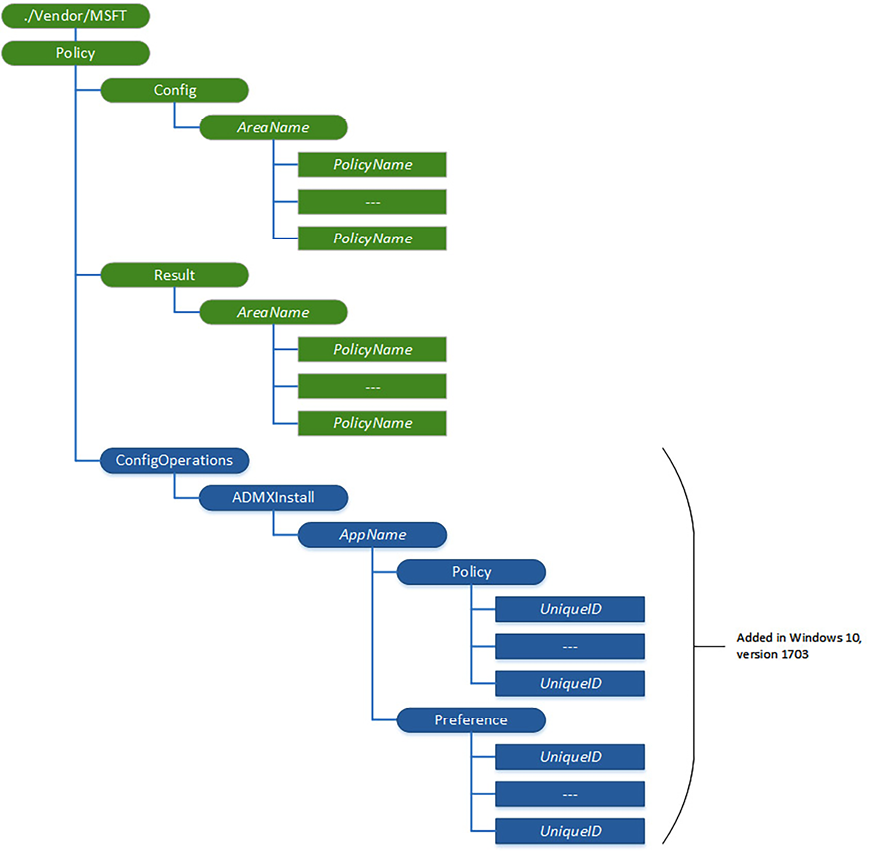
Figure 9.1: CSP policy tree
By using ADMXInstall, you can add ADMX-backed policies for those Win32 or Desktop Bridge apps that have been added between OS releases. ADMX-backed policies are ingested by your device by using the CSP policy URI: ./Vendor/MSFT/Policy/ConfigOperations/ADMXInstall.
The OMA-URI string needs to go into the CSP policy URI:
./Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Applicationname/Policy/ADMXFileName../Vendor/MSFT/Policy/Config/remains the same for all machine-based policies that you deploy to the device.
Applicationname and ADMXFileName are user-defined. In this case, Applicationname is App1, and you can use the same name as ADMXFileName. Just remember that ADMXFileName needs to be unique, which means you cannot deploy two ADMX files with the same name on a device, as it will fail and any additional ADMX files will not be added to the device.
Here is the content of the ADMX file in my case – this could also have been Google Chrome, Microsoft Office, Internet Explorer, or others:
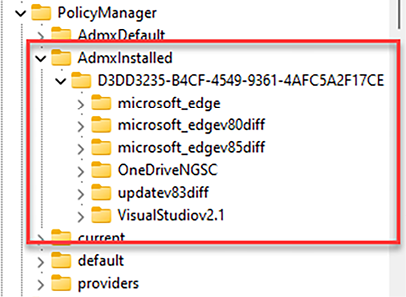
Figure 9.2: Registry entry for AdmxInstalled
Then, if you take a closer look at the registry, the first place where they are written is HKLM\SOFTWARE\MICROSOFT\PolicyManager\AdmxInstalled.
The policy is always declared under a GUID and with the name you gave the policy in Microsoft Intune when you created the policy.
Then, you will be able to see the naming of the policy category that you are using when creating a policy setting: HKLM\Software\Microsoft\PolicyManager\AdmxDefault
If the policy is a device policy, you will be able to see the direct results that apply to the devices in the following location: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device.
In the end, all a policy does on a Windows device is set some registry keys, and it is the same with MDM policies. All the policy settings go here: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\.
MDM policies are applied when a device syncs, either from Microsoft Intune or as part of the 8-hour schedule when a Windows device is running with MDM sync on.
For an IT admin to sync a device from Microsoft Intune, they need to start the Microsoft Intune admin center and follow these steps:
- Click Home | Devices | Windows | Windows devices.
- Search for the device you want to sync, and then select the device and click Sync. Intune will then try and reach out to the device through Windows Push Notification Service (WNS).
- You can read more about WNS in the next section.
Figure 9.3: Device sync
- In the same view, where you just selected a single device, you can also leverage Bulk Device Actions:
Figure 9.4: Bulk device actions
- Select Windows for OS.
- For Device type, select Cloud PCs or Physical devices.
- Select Sync as Device action:
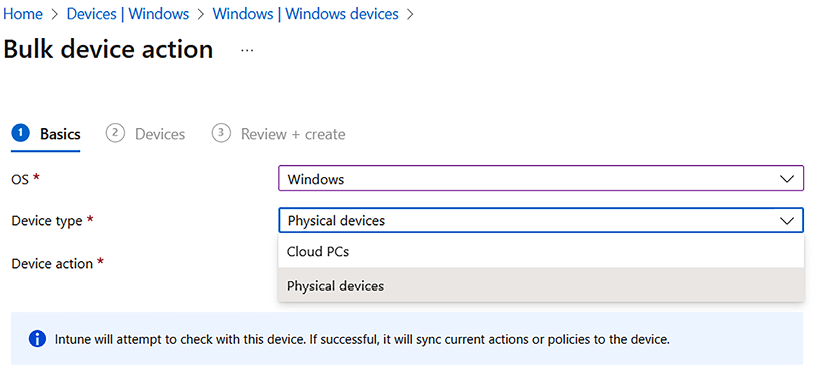
Figure 9.5: Bulk device action – Windows
- Then, you can select up to 100 devices that Microsoft Intune will reach out to and perform the sync:
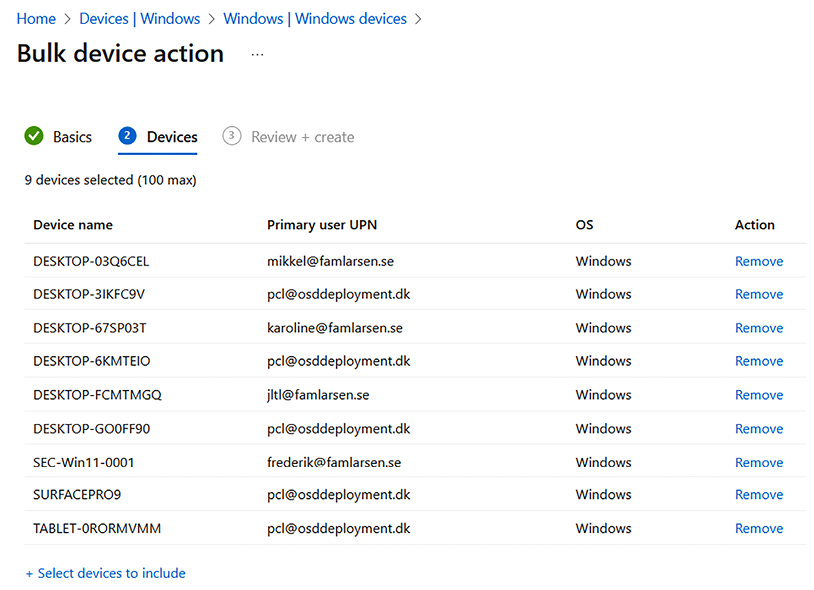
Figure 9.6: Bulk device action
When leveraging bulk device actions, Microsoft Intune uses WNS. In the next section, you will learn about how WNS works.

























































