Quick start – configuring the default security policy in PowerShell
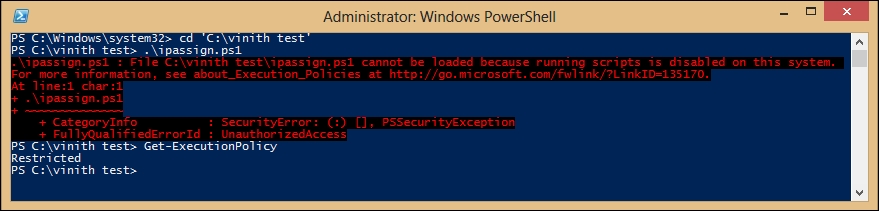
This section will give you an insight on the default script execution policy inbuilt in PowerShell 3.0. The execution policy determines if the PowerShell scripts' execution is disabled or enabled on the server. By default, the PowerShell script execution policy is set to Restricted in order to avoid any malicious code from running on your server; that means that scripts—including those you write yourself—won't run. You can verify the settings for your execution policy by typing the following in the PowerShell command prompt:
PS C:\> Get-ExecutionPolicy
You should now see the following screenshot:
If you want PowerShell to run any scripts that you write yourself or scripts downloaded from the Internet that have been signed by a trusted publisher, set your execution policy to RemoteSigned.
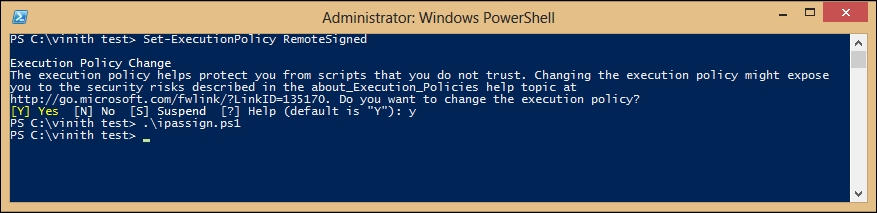
You can change the settings for your execution policy to RemoteSigned by typing the following in the PowerShell command prompt:
PS C:\> Set-ExecutionPolicy RemoteSigned
You should now see the following screenshot:
Alternatively, you can set the execution policy to All Signed / Unrestricted. Setting the execution policy to Unrestricted is insecure and not recommended in production environments.
The Set-ExecutionPolicy cmdlet changes the user preference for the Windows PowerShell execution policy by setting it in the registry HKLM\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell\ExecutionPolicy.
On a 64-bit OS, you need to run Set-ExecutionPolicy for 32-bit and 64-bit PSH separately. You can change the ExecutionPolicy setting just once by specifying it in parameter when launching PowerShell:
PS C:\> powershell.exe -ExecutionPolicy Unrestricted
In that case, the execution policy is set in the variable $env:PSExecutionPolicyPreference.
For a more detailed help on script signing, you can type in the following command in your PowerShell console:
PS C:\> Get-Help about_Signing
You should now see the following screenshot: