Detecting XSS vulnerabilities
XSS has three different types, but all of them have one thing in common—they derive from the input validation error to manage characters that are used to inject JavaScript code or HTML tags. So, we can use some inputs as shown in the following screenshot (which is a cheat sheet from the OWASP project), and add to the Intruder tool as payload:

A cheat sheet from the OWASP project
The way to detect XSS vulnerabilities is to find these codes without encoding or modifications in the responded HTML or that we did not get an error after injecting the testing strings.
To add the cheat sheet, use a similar process to adding the payload list to Intruder. Open the Intruder tool, click on the Payloads tab, and then select the Load button. Finally, mark all the parameters that you think are vulnerable, then click on Start attack, as shown in the following screenshot:
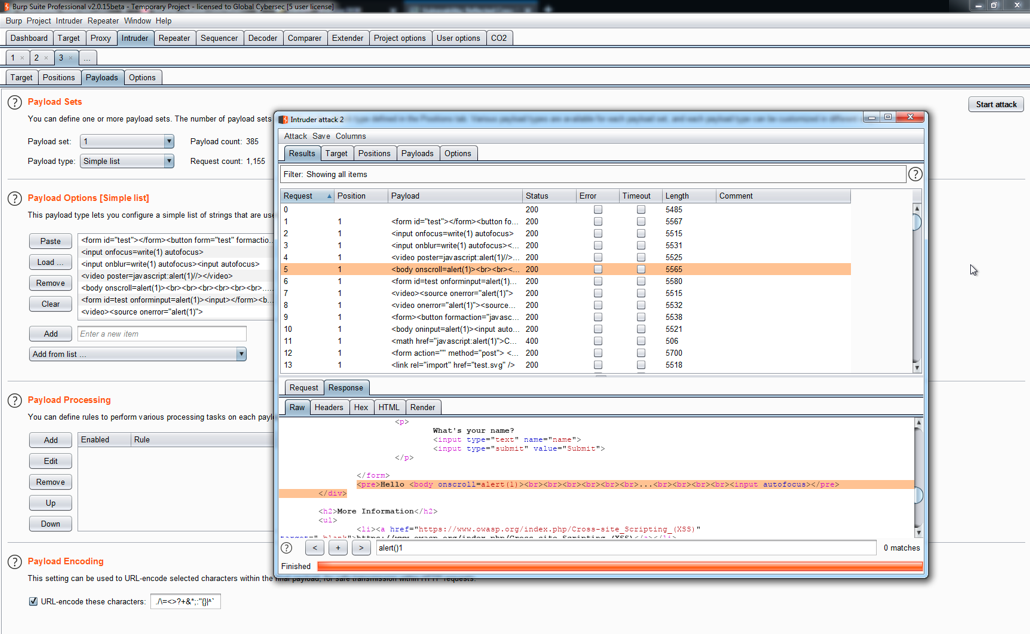
List of vulnerable parameters
In the preceding screenshot, we can see how all the strings were launched by Intruder...


























































